Introduction
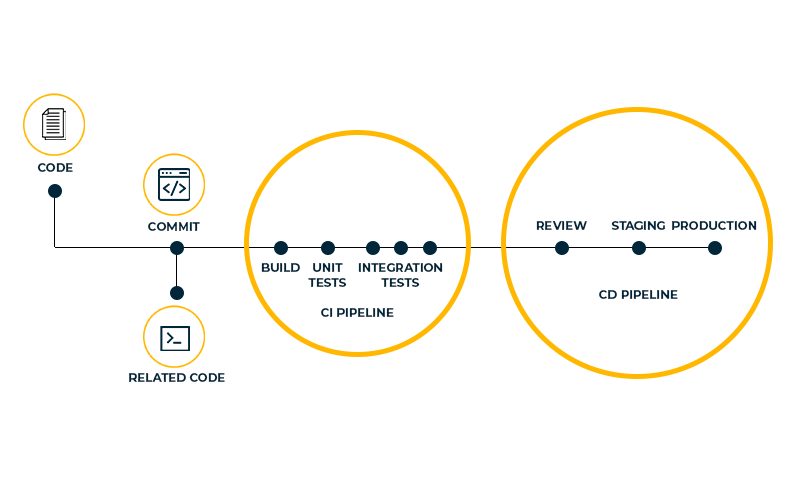
As software development processes become more complex, Continuous Integration (CI) plays a crucial role in streamlining and automating the process. However, ensuring the security of your CI pipeline is essential to minimize risks and protect sensitive data. In this blog post, we will discuss 10 key Continuous Integration security best practices that will help maintain a secure development environment.
- Secure Your CI Environment:
Make sure your CI server is protected with firewalls, strong authentication mechanisms, and role-based access controls. This prevents unauthorized access and ensures that only authorized team members can access the CI environment.
- Keep Tools and Dependencies Up-to-Date:
Regularly update your CI tools, plugins, and dependencies to address known security vulnerabilities. This helps maintain the security and stability of your pipeline.
- Encrypt Sensitive Data:
Use encryption for storing sensitive data, such as API keys, tokens, and passwords, in your CI environment. This helps protect sensitive information from being exposed or accessed by unauthorized users.
- Regularly Scan for Vulnerabilities:
Implement automated vulnerability scanning tools to identify and address security issues in your codebase, dependencies, and environment. Regular scans can help detect potential threats before they become critical.
- Implement Strong Access Controls:
Limit access to your CI environment based on the principle of least privilege. Ensure team members have the appropriate permissions for their roles and restrict access to sensitive parts of the system.
- Use Code Signing:
Implement code signing to ensure the integrity of your code and confirm the source of the code being deployed. This helps prevent unauthorized or tampered code from being integrated into your pipeline.
- Implement Secure Coding Practices:
Train your developers on secure coding practices and enforce them throughout the development process. Secure coding helps reduce the number of vulnerabilities introduced into the software.
- Regularly Audit and Monitor:
Conduct regular audits of your CI environment and closely monitor logs and alerts for suspicious activity. This helps detect potential security breaches and enables prompt response to incidents.
- Use Container Security Best Practices:
If you use containers, follow best practices for securing them, such as using minimal base images, scanning for vulnerabilities, and implementing runtime security. This helps ensure the security of your containerized applications and infrastructure.
- Establish a Security Incident Response Plan:
Create a plan for handling security incidents in your CI environment, including roles, responsibilities, and communication channels. A well-defined incident response plan enables your team to quickly react to and recover from security breaches.
Conclusion
Implementing Continuous Integration security best practices is vital to safeguarding your CI pipeline and maintaining a secure development environment. By following these recommendations, you can minimize risks, protect sensitive data, and promote a security-conscious culture within your development team.
Post a comment Cancel reply
Related Posts
Top SOC Tools: An Exhaustive Guide to the Most Popular Security Operations Center Solutions
As a cybersecurity expert with years of hands-on experience in Security Operations Centers (SOCs), I’ve…
Securing IoT Devices with Zero Trust Architecture: An Exhaustive Guide
As a cybersecurity expert, I’ve witnessed firsthand the explosive growth of the Internet of Things…
Mastering Secure SDLC: An In-Depth Guide to Integrating Security into the Secure Software Development Life Cycle
In the ever-evolving landscape of cybersecurity, integrating security into the Secure Software Development Life Cycle…
Mastering Passive Information Gathering: An In-Depth Guide to Open-Source Intelligence (OSINT)
In the realm of cybersecurity and ethical hacking, Passive Information Gathering plays a crucial role…