We're providing Secure Debug consultancy services. Secure Debug is a cybersecurity consultancy company that offer secure code audit, penetration testing, software development in cybersecurity era as well as cybersecurity pieces of training.
Read More
Penetration Testing
Simulating cyber-attacks on your systems, networks, and applications to identify vulnerabilities before they can be exploited by malicious actors.
Contact Us
Security Awareness & Training
Empowering individuals and teams with the knowledge and skills to recognize and mitigate security threats, fostering a proactive cybersecurity culture.
Contact Us
Infrastructure Security
Protecting the foundational IT components—including servers, networks, and storage systems—from threats and vulnerabilities, ensuring uninterrupted business operations and data integrity.
Contact Us
Identity and Access Management (IAM)
Managing and verifying user identities, ensuring the right individuals have appropriate access to resources, and maintaining secure and compliant user lifecycle processes.
Contact Us
Application Security
Application Security focuses on ensuring software applications are protected from external and internal threats, safeguarding data and maintaining functionality as intended.
Contact Us
Security Operations Center (SOC)
Providing round-the-clock monitoring, detection, and rapid response to security threats, ensuring continuous protection and minimizing potential breaches.
Contact Us
Endpoint Security
Defending individual devices, such as computers and mobile units, from cyber threats, ensuring that entry points for malicious activities are effectively safeguarded.
Contact Us
Data Protection & Privacy
Safeguarding sensitive data from breaches and unauthorized access, while ensuring compliance with global privacy regulations and standards.
Contact Us
Incident Response & Threat Hunting
Proactively identifying and mitigating threats while providing rapid response to security breaches, ensuring minimal impact and swift recovery.
Contact Us
Cloud Security
Ensuring the safety of data, applications, and services in the cloud, protecting against unauthorized access, data breaches, and other potential threats.
Contact Us
Cybersecurity Strategy & Governance & Audit
Designing strategic cybersecurity frameworks and ensuring organizational adherence, complemented by thorough audits to validate compliance and effectiveness against evolving threats.
Contact Us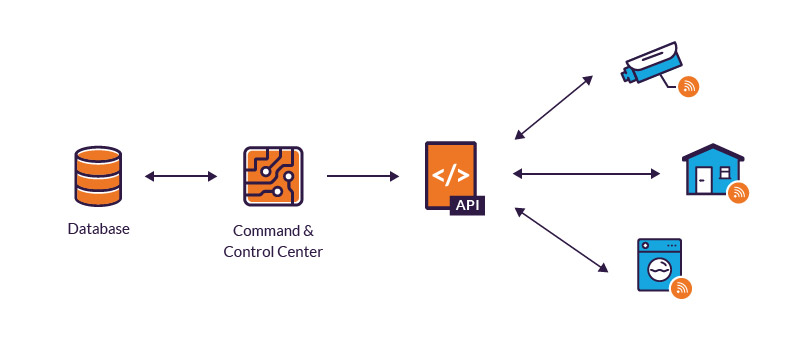
IoT (Internet of Things) Security
Securing interconnected devices and systems, preventing vulnerabilities in the vast IoT landscape, and ensuring data transmitted remains confidential and untampered.
Contact UsOur Mission
Our mission is to provide our clients with the best penetration testing services and the most current cyber security products, elevating the security of their businesses to the highest level."
Our Core Values
- We understand and meet the needs of our clients.
- We prioritize quality in our services and products to provide our clients with the best results.
- We strive to be a reliable partner by delivering on our promises to our clients.
- We keep up with industry innovations and constantly improve our services and products.
Our Vision
Our vision is to take our clients' cyber security to the next level, ensuring the security of their businesses and assets.







