The Power of Threat Intelligence Platforms in Securing Your Digital Assets
The Power of Threat Intelligence Platforms in Securing Your Digital Assets As the digital landscape evolves, so do the threats that organizations face. Cybercriminals are becoming more sophisticated, employing advanced techniques to breach security defenses and steal sensitive data. In this ever-changing landscape, it is crucial for organizations to stay one step ahead of these…
Read morePOSTED BY
Okan YILDIZ
Best Practices for Remote Access Security Controls
Best Practices for Remote Access Security Controls Welcome to Secure Debug’s cybersecurity blog! In this post, we will delve into the world of remote access security controls and explore the best practices to ensure your organization’s data remains secure. Introduction Remote access is an essential component of modern business operations, enabling employees to connect to…
Read morePOSTED BY
Okan YILDIZ
Developing a Comprehensive Cybersecurity Policy Framework
Developing a Comprehensive Cybersecurity Policy Framework In today’s digital landscape, cybersecurity has become a critical concern for organizations of all sizes. With the increasing frequency and sophistication of cyber threats, having a well-defined cybersecurity policy framework is essential to protect sensitive data, ensure business continuity, and maintain customer trust. In this blog post, we will…
Read morePOSTED BY
Okan YILDIZ
The Power of Security Information and Event Management (SIEM)
The Power of Security Information and Event Management (SIEM) As cyber threats continue to evolve and become more sophisticated, organizations must strengthen their cybersecurity posture to protect their sensitive data and systems. One crucial tool in this arsenal is Security Information and Event Management (SIEM). SIEM is a comprehensive approach to security management that enables…
Read morePOSTED BY
Okan YILDIZ
The Rising Threat of Cyber Terrorism: Exploring the Dark Side of the Digital World
With the rapid advancements in technology, the world has become increasingly interconnected, providing us with numerous benefits. However, this digital revolution has also given rise to a new and sinister form of terrorism – cyber terrorism. In this blog post, we will delve into the depths of this emerging threat, exploring its various facets and…
Read morePOSTED BY
Okan YILDIZ
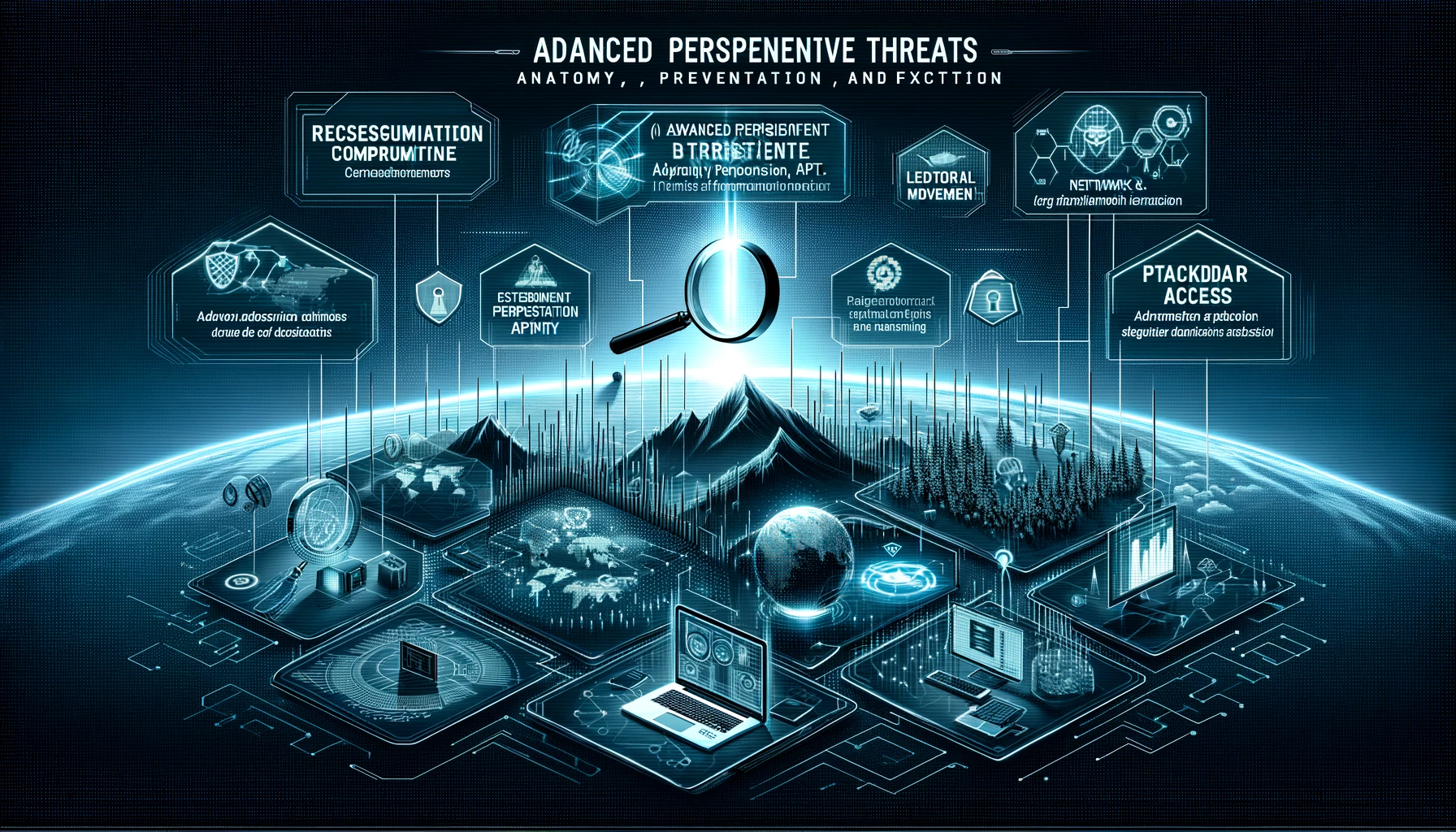
Demystifying Advanced Persistent Threats (APT): Anatomy, Prevention, and Detection
Demystifying Advanced Persistent Threats (APT): Anatomy, Prevention, and Detection Welcome to the Secure Debug blog, where we dive deep into the world of cybersecurity. In this post, we will unravel the enigma surrounding Advanced Persistent Threats (APT), exploring their anatomy, prevention strategies, and detection techniques. APTs represent one of the most dangerous and sophisticated cyber…
Read morePOSTED BY
Okan YILDIZ
Secure Remote Work Solutions: Ensuring Cybersecurity in the Age of Remote Work
Introduction Welcome to the Secure Debug blog, where we discuss the latest cybersecurity trends and provide valuable insights to keep your digital assets safe. In this blog post, we will explore the importance of secure remote work solutions and how they can protect your organization from cyber threats in the age of remote work. The…
Read morePOSTED BY
Okan YILDIZ
Enhancing Blockchain Security: A Comprehensive Guide
Enhancing Blockchain Security: A Comprehensive Guide Blockchain technology has revolutionized the way we conduct transactions and store data. Its decentralized nature and cryptographic techniques offer unparalleled security benefits. However, like any other technological innovation, blockchain is not immune to security threats. In this blog post, we delve into the world of block chain security and…
Read morePOSTED BY
Okan YILDIZ
Cyber Security in Online Gaming Platforms: Cybersecurity Measures and Best Practices
Protecting Online Gaming Platforms: Cybersecurity Measures and Best Practices Online gaming has witnessed a remarkable surge in popularity over the years, attracting millions of users who engage in virtual adventures and competitive battles. However, this rise in popularity has also made online gaming platforms an attractive target for cybercriminals seeking to exploit vulnerabilities and gain…
Read morePOSTED BY