Comprehensive Guide to Implementing OWASP SAMM v2
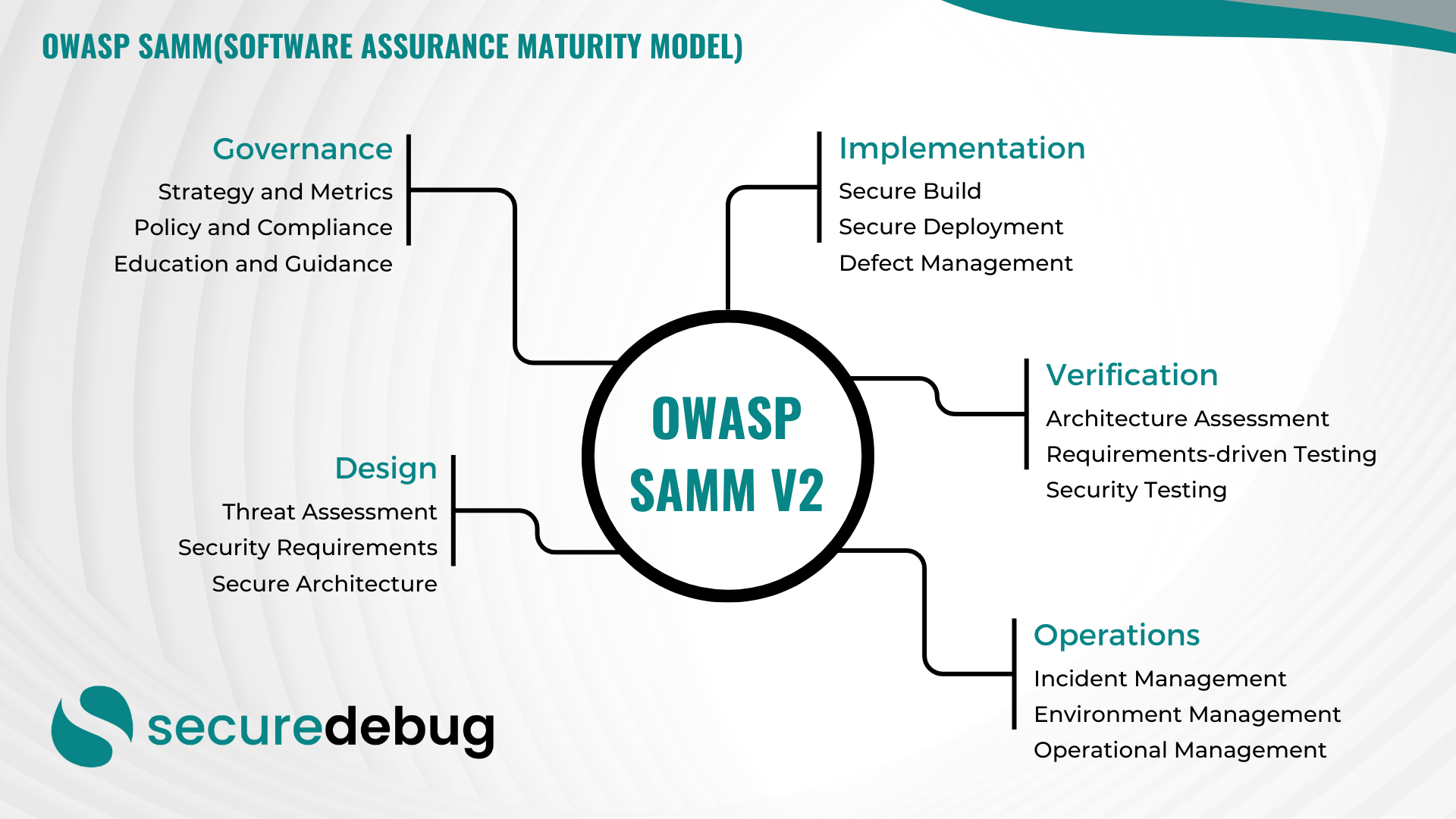
Comprehensive Overview of OWASP Software Assurance Maturity Model (SAMM) Version 2 Introduction to OWASP SAMM v2 The OWASP Software Assurance Maturity Model (SAMM) Version 2 is an evolutionary framework designed to assist organizations in developing, enhancing, and maintaining a robust software security posture. As part of the Open Web Application Security Project (OWASP), SAMM provides…
Read morePOSTED BY
Secure Debug
Enhancing Agricultural Cybersecurity: Protecting the Heart of Our Food Supply Chain
The Role of Cybersecurity in Agriculture As the agriculture industry becomes increasingly digitized, the need for robust cybersecurity measures has never been more critical. With the adoption of IoT devices, AI-driven technologies, and cloud-based systems, farmers are now more vulnerable to cyber threats than ever before. It’s essential for agricultural organizations to prioritize cybersecurity to…
Read morePOSTED BY
Okan YILDIZ
Securing Applications Against SQL Injection Vulnerabilities
Securing Applications Against SQL Injection Vulnerabilities SQL injection attacks have been a persistent threat to web applications, allowing malicious actors to manipulate databases and access sensitive information. As a cybersecurity firm, it is crucial to understand the importance of securing applications against SQL injection vulnerabilities to protect data integrity and user privacy. Understanding SQL Injection…
Read morePOSTED BY
Okan YILDIZ
Threat Modeling for Cloud Applications
Threat Modeling for Cloud Applications: Enhancing Security in the Digital Age As businesses increasingly migrate their operations to the cloud, the need for robust cybersecurity measures has become more critical than ever. Threat modeling for applications is a proactive approach to identifying and mitigating potential security threats before they can be exploited by malicious actors.…
Read morePOSTED BY
Okan YILDIZ
Threat Modeling for IoT Devices
Understanding Threat Modeling for IoT Devices As the Internet of Things (IoT) continues to expand, the need for robust cybersecurity measures becomes increasingly crucial. Threat modeling is a proactive approach to identifying potential security vulnerabilities and mitigating risks in IoT devices. By understanding the potential threats and attack vectors, organizations can better protect their devices…
Read morePOSTED BY
Okan YILDIZ
Secure Coding Practices in Python
Secure Coding Practices in Python Python is a powerful and versatile programming language used by developers worldwide. However, with great power comes great responsibility. In today’s digital age, cybersecurity threats are on the rise, making it crucial for developers to follow secure coding practices to protect their applications from potential vulnerabilities. Here are some essential…
Read morePOSTED BY
Okan YILDIZ
Encryption Best Practices for Data Security
Encryption Best Practices for Data Security Welcome to the Secure Debug blog, where we discuss the latest trends and best practices in cybersecurity. In this blog post, we will delve into the world of encryption and explore the best practices for ensuring data security. Encryption is a crucial component of any robust cybersecurity strategy, as…
Read morePOSTED BY
Okan YILDIZ
The Role of Threat Modeling in DevSecOps
The Role of Threat Modeling in DevSecOps As cybersecurity threats continue to evolve, organizations must adopt robust security practices to protect their digital assets. DevSecOps, a methodology that combines development, security, and operations, has gained significant traction in recent years. One critical aspect of DevSecOps that plays a vital role in ensuring secure software development…
Read morePOSTED BY
Okan YILDIZ
Secure Coding Practices in Python
Secure Coding Practices in Python Python is a popular programming language known for its simplicity and readability. However, when it comes to cybersecurity, ensuring secure coding practices is crucial to protect sensitive data and prevent potential vulnerabilities. In this blog post, we will explore some important secure coding practices in Python that can help developers…
Read morePOSTED BY
Okan YILDIZ
Effective Remote Code Execution (RCE) Defense Strategies
Introduction Remote Code Execution (RCE) is a critical vulnerability that can allow attackers to gain unauthorized access to a system, execute arbitrary code, and potentially take complete control. To defend against RCE attacks, organizations must adopt robust defense strategies that mitigate these risks effectively. Understanding Remote Code Execution Before delving into defense strategies, it is…
Read morePOSTED BY