Comprehensive Overview of OWASP Software Assurance Maturity Model (SAMM) Version 2
Introduction to OWASP SAMM v2
The OWASP Software Assurance Maturity Model (SAMM) Version 2 is an evolutionary framework designed to assist organizations in developing, enhancing, and maintaining a robust software security posture. As part of the Open Web Application Security Project (OWASP), SAMM provides a community-driven pathway towards understanding and improving security in software development.
Definition of OWASP SAMM v2
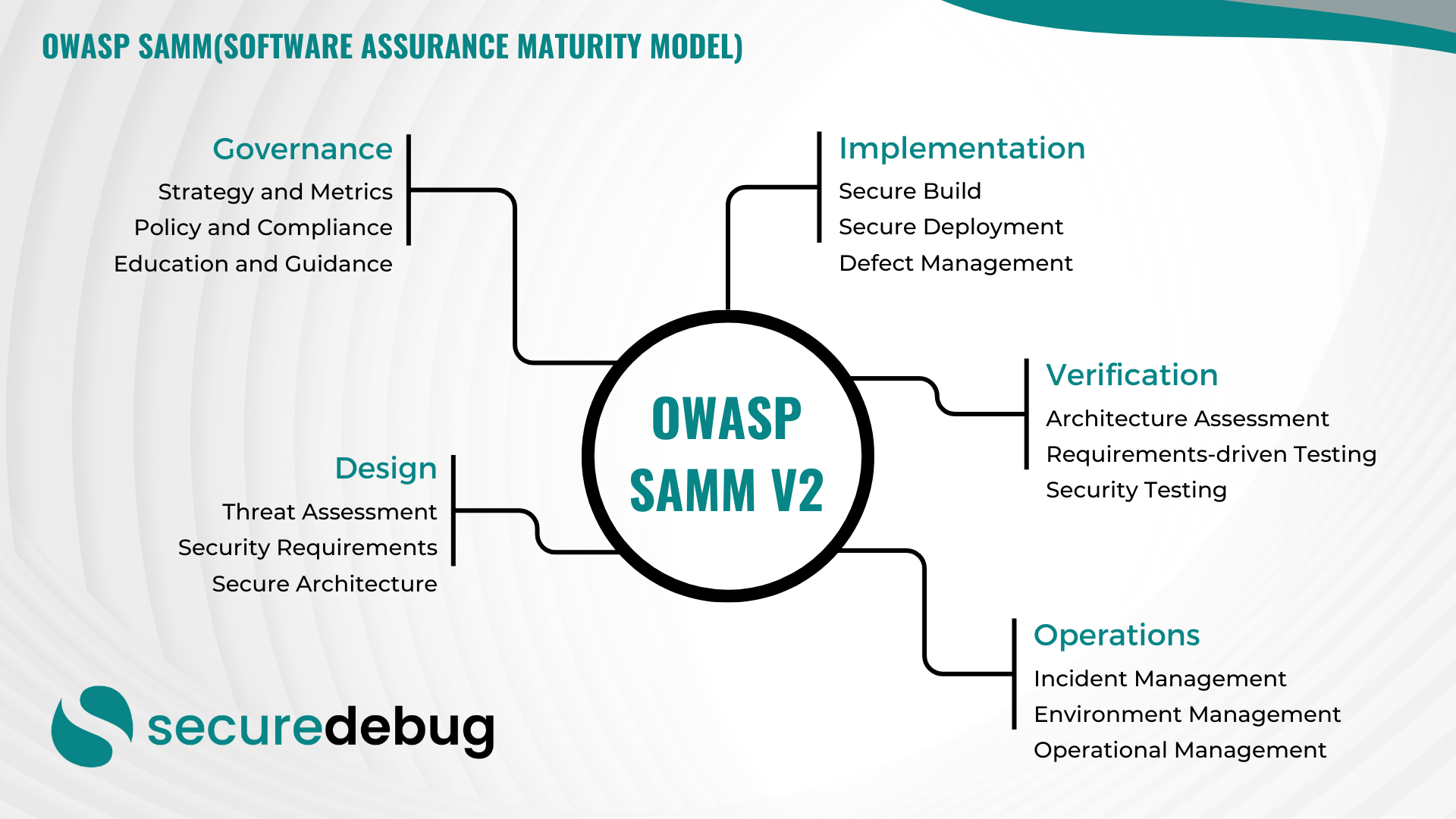
OWASP SAMM v2 is a model that offers a comprehensive and customizable approach to integrating security into software development processes. It is structured around key business functions, which encompass governance, design, implementation, verification, and operations. Each function is broken down into three security practices, making the model both extensive and adaptable to varying organizational needs.
History and Development
Originally launched in 2009, the OWASP SAMM framework was developed to provide an effective and measurable way for organizations to analyze and improve their software security posture. By 2020, rapid advancements in software development practices necessitated an update, leading to the release of Version 2. This update was collaboratively authored by an international group of security experts, and it reflects a comprehensive understanding of modern security challenges. It incorporates feedback from the user community, lessons learned from its practical applications, and aligns with contemporary technologies and methodologies such as DevOps and cloud computing.
Why Use OWASP SAMM v2?
Organizations adopt OWASP SAMM v2 for several strategic reasons:
- Structured Security Strategy: It provides a clear, structured strategy for integrating security into software development, helping organizations address security in a consistent and comprehensive manner.
- Tailored Risk Management: The model is adaptable, allowing organizations to focus on specific practices that best address their unique risks and threat landscape.
- Continuous Improvement: OWASP SAMM v2 encourages a cycle of continuous improvement in security practices through its maturity levels, which guide organizations from initial ad hoc practices to advanced, optimized processes.
- Benchmarking Capabilities: By using the model, organizations can measure their security practices against an established benchmark, facilitating internal assessments and regulatory compliance.
Who Can Use OWASP SAMM v2?
The versatility of OWASP SAMM v2 makes it suitable for a wide array of users:
- Enterprises of All Sizes: From small startups to large enterprises, any organization that develops software can utilize SAMM to better integrate security into their development lifecycles.
- Across Various Industries: Industries such as finance, healthcare, education, and government, where software plays a critical role in operations, find particular value in the structured approach SAMM provides.
- Security Professionals and Consultants: For those tasked with assessing or improving organizational security, SAMM serves as a detailed roadmap and toolkit for enhancing software security maturity.
Implementation Strategy
Implementing OWASP SAMM v2 involves several key steps:
- Initial Self-Assessment: Organizations begin by conducting a baseline assessment to determine their current maturity level across different security practices.
- Goal Setting: Based on the assessment results, specific, measurable goals are set for each practice area, tailored to the organization’s security needs and business objectives.
- Incremental Improvement: Organizations then work on meeting these goals through incremental improvements, systematically addressing each area of the model.
- Regular Review and Adaptation: Regular reviews are conducted to assess progress and adapt the strategy as necessary, ensuring it remains relevant to the changing technology landscape and business requirements.
Conclusion
OWASP SAMM v2 offers a dynamic and strategic framework that helps organizations not just comply with security standards but integrate security as a fundamental component of software development. By following SAMM, organizations can aspire to not only protect their assets and data but also foster a culture of security awareness and resilience.
Functional Areas of OWASP SAMM
Detailed Overview of OWASP SAMM v2 Framework Functional Areas and Security Practices
The OWASP Software Assurance Maturity Model (SAMM) Version 2 is structured around five key functional areas, each divided into specific security practices. These practices are further detailed in two streams per practice, addressing different aspects of security implementation. Here is a breakdown of each functional area and their respective security practices:
1. Governance
Governance focuses on establishing leadership and organizational structures that foster a secure software development culture.
- Strategy & Metrics
- Create & Promote: Developing and promoting a security strategy that aligns with business objectives.
- Measure & Improve: Implementing metrics to measure the effectiveness of security practices and continuously improving them based on these metrics.
- Policy & Compliance
- Policy & Standards: Developing comprehensive security policies and standards that are consistently applied across the organization.
- Compliance Management: Ensuring that all software practices meet internal compliance controls and external regulatory requirements.
- Education & Guidance
- Training & Awareness: Conducting regular security training and awareness programs to enhance employee understanding and engagement with security practices.
- Organization & Culture: Building a security-conscious organizational culture through continuous education and proactive security practices.
2. Design
Design ensures that security is integrated into the software development lifecycle from the earliest stages.
- Threat Assessment
- Application Risk Profile: Creating risk profiles for applications to identify specific security needs.
- Threat Modeling: Systematically modeling potential threats to design robust security measures.
- Security Requirements
- Software Requirements: Defining security requirements that are specific to software functionalities and operational needs.
- Supplier Security: Ensuring that third-party suppliers and partners adhere to security requirements that protect the supply chain.
- Secure Architecture
- Architecture Design: Designing software architectures that inherently prioritize security features and resilience.
- Technology Management: Managing technology stacks to ensure they are updated, secure, and capable of supporting secure applications.
3. Implementation
Implementation covers the development and build processes of software, ensuring secure practices are followed.
- Secure Build
- Build Process: Integrating security into the software build process to ensure consistent application of security practices.
- Software Dependencies: Managing software dependencies to avoid vulnerabilities from third-party components.
- Secure Deployment
- Deployment Process: Ensuring secure deployment practices that maintain the integrity and security of software in production.
- Secret Management: Managing and protecting secrets, such as keys and credentials, to prevent unauthorized access.
- Defect Management
- Defect Tracking: Systematically tracking and managing defects to ensure they are addressed in a timely and secure manner.
- Metrics & Feedback: Using defect metrics and feedback to improve the security of the development process.
4. Verification
Verification ensures that all security measures are properly tested and validated.
- Architecture Assessment
- Architecture Validation: Validating the security of software architectures against defined security standards.
- Architecture Compliance: Ensuring architectures comply with both internal and external security requirements.
- Requirements-driven Testing
- Control Verification: Verifying that security controls meet the intended security requirements and are effective.
- Misuse/Abuse Testing: Testing how the system copes with misuse or malicious actions, ensuring resilience.
- Security Testing
- Scalable Baseline: Developing scalable security testing procedures that can grow with the system.
- Deep Understanding: Gaining a deep understanding of potential vulnerabilities and security challenges through thorough testing.
5. Operations
Operations focus on maintaining and managing software in its operational state to ensure ongoing security.
- Incident Management
- Incident Detection: Developing capabilities to detect security incidents promptly.
- Incident Response: Responding effectively to security incidents to minimize impact and restore normal operations.
- Environment Management
- Configuration Hardening: Hardening configurations to protect against vulnerabilities.
- Patch & Update: Regularly updating and patching systems to protect against known vulnerabilities.
- Operational Management
- Data Protection: Ensuring that data is protected through effective security measures throughout its lifecycle.
- Legacy Management: Managing legacy systems to ensure they remain secure or are phased out in favor of more secure solutions.
Practices Under Each Functional Area
Each functional area within the OWASP SAMM v2 framework includes specific security practices. These practices are designed to be implemented progressively, with the aim of achieving a comprehensive and mature software security posture. Here’s a detailed look at the practices under each functional area:
1. Governance
Governance involves establishing a strategic foundation for security within the organization, aligning it with business goals, and ensuring compliance with relevant standards and regulations.
- Strategy & Metrics
- Create & Promote: Develop a clear security strategy that aligns with organizational objectives and promotes security awareness throughout the organization.
- Measure & Improve: Establish metrics to measure the effectiveness of the security strategy and continuously improve it based on these measurements.
- Policy & Compliance
- Policy & Standards: Formulate and enforce comprehensive security policies and standards that are applicable across the organization.
- Compliance Management: Ensure ongoing compliance with internal policies and external regulatory requirements through regular audits and updates.
- Education & Guidance
- Training & Awareness: Implement continuous security training and awareness programs to educate employees about security best practices.
- Organization & Culture: Foster a security-conscious organizational culture by integrating security principles into everyday business activities and decisions.
2. Design
Design focuses on embedding security into the software development process from the initial stages, ensuring that potential risks are addressed early on.
- Threat Assessment
- Application Risk Profile: Develop risk profiles for applications to identify specific security needs and prioritize risk mitigation efforts.
- Threat Modeling: Conduct systematic threat modeling to identify and address potential threats to the software early in the design phase.
- Security Requirements
- Software Requirements: Define clear and actionable security requirements for software projects, ensuring that security is considered in all aspects of software development.
- Supplier Security: Ensure that third-party suppliers and partners adhere to security requirements that protect the supply chain and maintain overall security integrity.
- Secure Architecture
- Architecture Design: Design software architectures that incorporate robust security controls and are resilient against identified threats.
- Technology Management: Manage and maintain the technology stack to ensure it supports secure application development and deployment.
3. Implementation
Implementation involves ensuring that secure coding and development practices are followed during the software development lifecycle.
- Secure Build
- Build Process: Integrate security into the software build process to ensure that security measures are applied consistently.
- Software Dependencies: Manage software dependencies to prevent vulnerabilities arising from third-party components and libraries.
- Secure Deployment
- Deployment Process: Establish secure deployment processes to maintain the integrity and security of software when it is moved to production environments.
- Secret Management: Implement and maintain robust secret management practices to protect sensitive information such as keys and credentials.
- Defect Management
- Defect Tracking: Systematically track and manage defects to ensure they are addressed promptly and securely.
- Metrics & Feedback: Use metrics and feedback from defect management to continuously improve the security of the software development process.
4. Verification
Verification ensures that all security controls and measures are correctly implemented and effective.
- Architecture Assessment
- Architecture Validation: Regularly validate the security of software architectures against established security standards.
- Architecture Compliance: Ensure that software architectures comply with internal security policies and external regulations.
- Requirements-driven Testing
- Control Verification: Verify that security controls meet the defined security requirements and are effective in mitigating risks.
- Misuse/Abuse Testing: Conduct testing to identify how the system handles misuse or malicious actions, ensuring robustness against such activities.
- Security Testing
- Scalable Baseline: Develop scalable security testing procedures that can adapt as the system grows.
- Deep Understanding: Gain a thorough understanding of potential vulnerabilities through comprehensive and rigorous security testing.
5. Operations
Operations focus on maintaining and enhancing the security of software in the production environment.
- Incident Management
- Incident Detection: Develop capabilities to detect security incidents promptly, minimizing potential damage.
- Incident Response: Establish and maintain an effective incident response process to address and recover from security incidents efficiently.
- Environment Management
- Configuration Hardening: Ensure that the operational environment is securely configured to resist attacks.
- Patch & Update: Regularly patch and update systems to protect against known vulnerabilities.
- Operational Management
- Data Protection: Implement robust data protection measures to safeguard sensitive information throughout its lifecycle.
- Legacy Management: Manage legacy systems to ensure they remain secure or are replaced with more secure alternatives.
How Are Levels Calculated in OWASP SAMM v2?
OWASP SAMM v2 provides a structured approach to assess and improve the maturity of software security practices within an organization. The model defines clear levels and criteria, uses a systematic evaluation process, and employs a scoring system to measure progress. Here’s a detailed look at how levels are calculated and strategies for improvement:
Level Definitions and Criteria
OWASP SAMM v2 defines three maturity levels for each security practice within the framework. These levels indicate the progression from basic, ad-hoc security practices to advanced, optimized processes:
- Level 1 – Initial: At this level, security practices are often informal, reactive, and inconsistently applied across projects. The organization has started to recognize the importance of security, but practices are not standardized.
- Criteria: Basic awareness and ad-hoc implementation of security practices. Initial efforts to address security concerns as they arise.
- Level 2 – Defined: Security practices are documented, repeatable, and consistently applied across similar projects. There is a proactive approach to managing security, and the organization begins to integrate security requirements into the development lifecycle.
- Criteria: Standardized procedures and policies are in place. Security requirements are defined and consistently implemented. There is evidence of proactive risk management.
- Level 3 – Advanced: Security practices are well-defined, optimized, and continuously improved based on metrics and feedback. The organization demonstrates a high level of security maturity with practices integrated deeply into the development lifecycle.
- Criteria: Advanced and automated security practices are implemented. Continuous monitoring, measurement, and improvement of security processes. Demonstrated ability to handle complex security challenges effectively.
Evaluation Process
The evaluation process involves several steps to accurately assess the maturity level of an organization’s security practices:
- Initial Assessment:
- Self-Assessment: Organizations start by conducting a self-assessment to evaluate their current security practices against the SAMM criteria.
- Documentation Review: Collect and review relevant documentation, policies, and procedures related to security practices.
- Gap Analysis:
- Identify gaps between current practices and the desired maturity level.
- Prioritize areas that need improvement based on risk and impact.
- Interviews and Workshops:
- Conduct interviews with key stakeholders, including security teams, developers, and management.
- Facilitate workshops to gather detailed insights and validate self-assessment findings.
- Final Scoring:
- Assign scores based on the evaluation of practices against the SAMM criteria.
- Use these scores to determine the current maturity level for each security practice.
Scoring System
The scoring system in OWASP SAMM v2 provides a quantitative measure of maturity for each security practice. The scoring is based on the following components:
- Practice Coverage: Extent to which security practices are implemented across the organization.
- Consistency: Degree of consistency in applying security practices across different projects and teams.
- Effectiveness: How effective the security practices are in achieving their intended goals and mitigating risks.
Each practice is scored on a scale, typically ranging from 0 (not implemented) to 3 (fully implemented and optimized). The scores are then aggregated to provide an overall maturity level for each functional area.
Strategies for Level Advancement
To advance through the maturity levels, organizations should adopt strategic approaches tailored to their specific needs and current maturity state:
- Resource Allocation:
- Investment in Tools and Training: Allocate resources for security tools, training programs, and skilled personnel.
- Budget for Continuous Improvement: Ensure there is ongoing investment in improving security practices.
- Process Integration:
- Embed Security in the SDLC: Integrate security practices into every stage of the software development lifecycle.
- Standardize Procedures: Develop and enforce standardized security procedures and policies.
- Continuous Improvement:
- Regular Reviews and Audits: Conduct regular reviews and audits of security practices to identify areas for improvement.
- Feedback Loops: Establish feedback loops to continuously refine and enhance security practices based on lessons learned.
- Stakeholder Engagement:
- Involve Key Stakeholders: Engage all relevant stakeholders, including developers, management, and external partners, in the security process.
- Promote a Security Culture: Foster a culture of security awareness and responsibility throughout the organization.
By following these strategies, organizations can systematically enhance their security posture and progress through the maturity levels in OWASP SAMM v2. This approach not only helps in achieving higher security maturity but also ensures that security practices are sustainable and effective in the long term.
Example Scenarios of OWASP SAMM v2 Implementation
Implementing OWASP SAMM v2 can significantly enhance an organization’s software security posture. To illustrate how SAMM can be applied in various contexts, here are detailed example scenarios across different sectors and organizational sizes, along with methods for evaluating and improving existing security levels and sharing success stories.
Different Sector Application Examples
Healthcare Sector
Scenario: A large hospital network seeks to protect patient data and ensure compliance with healthcare regulations like HIPAA.
Implementation Steps:
- Initial Assessment: Conduct a self-assessment using OWASP SAMM to identify current security practices and gaps.
- Governance: Develop a comprehensive security strategy and metrics aligned with HIPAA requirements. Implement policies and compliance management to ensure ongoing adherence to regulations.
- Design: Conduct threat assessments to identify risks specific to patient data systems. Define security requirements for all new software projects.
- Implementation: Implement secure build processes and software dependency management to prevent vulnerabilities.
- Verification: Perform architecture assessments and requirements-driven testing to validate security controls.
- Operations: Establish incident management protocols to detect and respond to security incidents promptly.
Outcome: Enhanced data protection, compliance with HIPAA, and improved ability to respond to security incidents.
Financial Services Sector
Scenario: A multinational bank aims to standardize security practices across its global software development teams.
Implementation Steps:
- Initial Assessment: Use OWASP SAMM to benchmark current security practices across different branches.
- Governance: Create a unified security policy and compliance framework applicable to all branches. Regularly measure and improve security metrics.
- Design: Develop risk profiles for financial applications and incorporate threat modeling.
- Implementation: Standardize secure build processes and enforce secure deployment practices globally.
- Verification: Conduct regular security testing and architecture assessments to ensure compliance with internal standards.
- Operations: Implement robust incident management and environment management practices to maintain security across all operations.
Outcome: Uniform security practices, reduced risk of data breaches, and enhanced regulatory compliance.
Education Sector
Scenario: A university seeks to secure its student information systems and ensure data privacy.
Implementation Steps:
- Initial Assessment: Conduct an assessment to identify existing security measures and gaps.
- Governance: Develop a security strategy that includes policies for data protection and compliance with educational regulations.
- Design: Perform threat assessments and establish security requirements for all software systems handling student data.
- Implementation: Implement secure coding practices and manage software dependencies carefully.
- Verification: Regularly test security controls through architecture validation and requirements-driven testing.
- Operations: Set up incident management processes and ensure continuous patching and updating of systems.
Outcome: Improved protection of student data and compliance with educational privacy regulations.
Scenarios for Small, Medium, and Large Enterprises
Small Business Example
Scenario: A tech startup with limited resources wants to protect its intellectual property and customer data.
Implementation Steps:
- Initial Assessment: Conduct a basic self-assessment to identify critical security gaps.
- Governance: Develop a simple security policy and provide basic security training to all employees.
- Design: Identify key threats and establish minimal security requirements for core applications.
- Implementation: Focus on secure build practices and manage dependencies to avoid common vulnerabilities.
- Verification: Conduct basic security testing and validate critical security controls.
- Operations: Implement a simple incident response plan and regularly update software to fix vulnerabilities.
Outcome: Basic but effective security practices that protect intellectual property and customer data.
Medium-sized Enterprise Example
Scenario: A growing e-commerce company wants to enhance the security of its online platform.
Implementation Steps:
- Initial Assessment: Use OWASP SAMM to assess current security practices and identify improvement areas.
- Governance: Establish comprehensive security policies and provide regular security training to developers and IT staff.
- Design: Perform detailed threat assessments and define security requirements for the e-commerce platform.
- Implementation: Implement secure coding practices and use automated tools for secure builds.
- Verification: Regularly test the platform’s security using advanced security testing techniques.
- Operations: Set up robust incident management and environment management processes to handle security incidents and maintain system security.
Outcome: Improved platform security, better protection against cyber threats, and increased customer trust.
Large Corporation Example
Scenario: A global manufacturer wants to ensure uniform security standards across its diverse software applications.
Implementation Steps:
- Initial Assessment: Conduct a comprehensive assessment of security practices across all global divisions.
- Governance: Develop a global security strategy and ensure all divisions comply with unified security policies.
- Design: Establish risk profiles for critical applications and incorporate threat modeling into the design phase.
- Implementation: Standardize secure build and deployment processes across all divisions.
- Verification: Implement regular security testing and architecture assessments globally.
- Operations: Maintain a centralized incident management system and ensure all systems are regularly patched and updated.
Outcome: Consistent and robust security practices across all divisions, reducing global security risks.
Evaluating and Improving Current Security Levels
Security Evaluation in a Software Development Firm
Scenario: A software development firm wants to evaluate and improve its current security posture.
Evaluation Process:
- Initial Self-Assessment: Conduct a SAMM-based self-assessment to identify current maturity levels across different security practices.
- Gap Analysis: Identify gaps between current practices and desired maturity levels.
- Interviews and Workshops: Gather detailed insights from stakeholders through interviews and workshops.
- Final Scoring: Score each practice based on SAMM criteria to determine the maturity level.
Improvement Strategies:
- Resource Allocation: Invest in security training and tools.
- Process Integration: Integrate security practices into the software development lifecycle.
- Continuous Improvement: Regularly review and update security practices based on feedback and metrics.
- Stakeholder Engagement: Engage all relevant stakeholders to foster a security-aware culture.
Outcome: A comprehensive understanding of current security maturity and a clear roadmap for improvement.
Success Stories and Experience Sharing
Retail Industry Success Story
Scenario: A retail giant successfully integrated OWASP SAMM practices, significantly enhancing their security posture.
Implementation Highlights:
- Governance: Developed a robust security strategy and policies.
- Design: Conducted thorough threat assessments and defined clear security requirements.
- Implementation: Standardized secure coding and deployment practices.
- Verification: Regularly tested security controls and validated architectures.
- Operations: Implemented a comprehensive incident management system.
Results: Significant reduction in data breaches, enhanced customer trust, and improved regulatory compliance.
Technology Firm’s Experience
Scenario: A technology firm shares its experience of implementing OWASP SAMM, focusing on secure architecture and build environments.
Key Learnings:
- Challenges: Initial resistance to change, resource allocation issues, and integrating security into existing workflows.
- Solutions: Conducted regular training, secured executive buy-in, and gradually integrated security practices into development processes.
- Outcomes: Enhanced security posture, reduced vulnerabilities, and a more security-conscious organizational culture.
Sharing Platform: The firm conducted workshops and webinars to share their journey, challenges, and solutions with other organizations, contributing to the wider adoption of SAMM practices.
Outcome: Increased awareness and adoption of OWASP SAMM practices across the industry.
Tables for OWASP SAMM v2 Implementation
Using tables to present information about OWASP SAMM v2 can help in visualizing the framework, assessing maturity levels, and tracking progress. Here are some example tables that you can use in your documentation.
Level and Practices Display Tables
Table 1: Maturity Levels and Key Practices
| Functional Area | Practice | Level 1 (Initial) | Level 2 (Defined) | Level 3 (Advanced) |
| Governance | Strategy & Metrics | Basic strategy awareness | Documented strategy with defined metrics | Continuous improvement with advanced metrics |
| Governance | Policy & Compliance | Ad-hoc policy application | Standardized policies, basic compliance | Full compliance management and automated monitoring |
| Governance | Education & Guidance | Occasional training sessions | Regular training programs and awareness campaigns | Integrated security culture with ongoing education |
| Design | Threat Assessment | Initial risk identification | Comprehensive threat modeling | Continuous threat assessment with real-time updates |
| Design | Security Requirements | Basic security requirements definition | Detailed and documented security requirements | Advanced and adaptive requirements management |
| Design | Secure Architecture | Ad-hoc security controls | Designed secure architecture | Fully integrated and optimized security architecture |
| Implementation | Secure Build | Basic secure build processes | Standardized secure build with automated tools | Advanced build security with continuous integration |
| Implementation | Secure Deployment | Manual secure deployment | Standardized deployment processes | Automated and monitored secure deployment |
| Implementation | Defect Management | Ad-hoc defect tracking | Formal defect tracking process | Advanced defect management with metrics and feedback |
| Verification | Architecture Assessment | Basic architecture review | Standardized architecture validation | Continuous architecture compliance and optimization |
| Verification | Requirements Testing | Initial control verification | Regular control verification | Advanced misuse/abuse testing and continuous testing |
| Verification | Security Testing | Basic security testing | Comprehensive security testing | Advanced security testing with deep vulnerability analysis |
| Operations | Incident Management | Basic incident response | Formal incident detection and response | Advanced incident management with continuous improvement |
| Operations | Environment Management | Initial configuration hardening | Standardized patch and update processes | Continuous environment management and optimization |
| Operations | Operational Management | Basic data protection | Standardized data and legacy management | Advanced operational management with data security integration |
Assessment Results Table
Table 2: Security Assessment Results
| Practice | Current Level | Findings | Recommendations |
| Strategy & Metrics | 1 | Lack of documented security strategy | Develop and document a comprehensive strategy |
| Policy & Compliance | 2 | Policies are in place but compliance is inconsistent | Implement regular compliance audits |
| Education & Guidance | 1 | Irregular training sessions | Establish a regular training program |
| Threat Assessment | 2 | Basic threat modeling exists | Enhance threat modeling with real-time updates |
| Security Requirements | 1 | Basic requirements defined | Develop detailed security requirements |
| Secure Architecture | 2 | Architecture design includes security controls | Optimize architecture with advanced controls |
| Secure Build | 1 | Basic secure build processes | Implement automated secure build tools |
| Secure Deployment | 1 | Manual deployment processes | Standardize and automate deployment processes |
| Defect Management | 2 | Formal defect tracking in place | Use metrics for continuous improvement |
| Architecture Assessment | 2 | Standard architecture validation | Regularly update validation processes |
| Requirements Testing | 1 | Initial control verification | Implement comprehensive control testing |
| Security Testing | 1 | Basic testing procedures | Develop advanced security testing protocols |
| Incident Management | 2 | Formal incident response but lacks continuous improvement | Implement continuous improvement processes |
| Environment Management | 2 | Standard patch and update processes | Optimize environment management practices |
| Operational Management | 1 | Basic data protection measures | Develop advanced data security protocols |
Progress Tracking and Reporting Tables
Table 3: Progress Tracking Table
| Date | Practice | Current Level | Target Level | Status | Next Steps |
| 2024-08-01 | Secure Build | 1 | 2 | In Progress | Implement automated build tools |
| 2024-08-01 | Security Testing | 2 | 3 | On Schedule | Develop advanced testing protocols |
| 2024-08-01 | Incident Management | 1 | 2 | Behind | Establish formal incident response plan |
| 2024-08-01 | Policy & Compliance | 2 | 3 | In Progress | Conduct regular compliance audits |
| 2024-08-01 | Education & Guidance | 1 | 2 | In Progress | Develop a regular security training program |
Annual Security Report Table
Table 4: Annual Security Report Table
| Year | Functional Area | Improvements Achieved | Outstanding Issues | Compliance Status |
| 2023 | Governance | Developed security strategy and metrics | Consistency in compliance enforcement | Compliant with major regulations |
| 2023 | Design | Implemented comprehensive threat modeling | Enhancing security requirements | Compliant |
| 2023 | Implementation | Standardized secure build process | Automating deployment processes | Partially Compliant |
| 2023 | Verification | Regular control verification | Advanced misuse/abuse testing | Compliant |
| 2023 | Operations | Formalized incident management process | Continuous improvement in incident response | Compliant |
Conclusion
At Secure Debug, we understand that in today’s rapidly evolving digital landscape, robust software security is more crucial than ever. Implementing a structured and comprehensive framework like OWASP SAMM v2 is essential for organizations seeking to protect their digital assets, ensure compliance, and build trust with their customers.
OWASP SAMM v2 offers a clear roadmap for assessing, improving, and measuring the maturity of your software security practices. By systematically addressing security across governance, design, implementation, verification, and operations, this model helps organizations to not only identify and mitigate risks but also to embed security into their core business processes.
Our team of experienced consultants at Secure Debug is dedicated to guiding you through each step of this journey. We offer tailored assessments, strategic planning, and hands-on support to help you achieve higher maturity levels in your security practices. Whether you are a small startup or a large enterprise, our services are designed to meet your unique needs and challenges.
By partnering with Secure Debug, you gain access to:
- Expert Knowledge: Our consultants bring deep expertise in OWASP SAMM and other leading security frameworks.
- Customized Solutions: We develop security strategies that align with your business goals and industry requirements.
- Continuous Improvement: We help you establish continuous improvement processes to keep your security posture up-to-date with evolving threats.
Investing in a structured security framework like OWASP SAMM v2 is not just about compliance—it’s about safeguarding your business’s future. With Secure Debug by your side, you can confidently navigate the complexities of software security, ensuring your systems are resilient, your data is protected, and your customers’ trust is maintained.
Let us help you turn security challenges into strengths. Contact Secure Debug today to learn more about how we can support your journey towards a more secure and mature software development lifecycle.
About Secure Debug Limited
Company Profile: Secure Debug Limited is a London-based cybersecurity services firm specializing in providing advanced security solutions to protect critical infrastructure and sensitive data. Our mission is to offer a secure digital environment for our clients by safeguarding their assets from cyber threats.
Our Services:
- Threat Assessment and Vulnerability Management: We conduct comprehensive analyses of our clients’ current security postures to identify potential threats and vulnerabilities. These assessments help organizations close security gaps and enhance their defense strategies.
- Incident Response and Recovery: In the event of a cyberattack, we provide rapid and effective response services to minimize damage and restore operations as quickly as possible. Post-incident analyses also help prepare for future threats.
- Continuous Monitoring and Security Operations: Our 24/7 monitoring services ensure that our clients’ networks are constantly overseen, detecting any anomalies. Our Security Operations Center (SOC) proactively takes measures against potential threats.
- Compliance and Regulatory Requirements: We assist our clients in achieving compliance with sector-specific and legal regulations, including GDPR, PCI-DSS, and ISO 27001, among others.
- Application Security: We provide robust application security services to ensure that our clients’ software is secure throughout its lifecycle. This includes code reviews, secure coding practices, and application security testing.
- DevSecOps: We integrate security practices into every phase of the software development lifecycle, fostering a culture where security is a shared responsibility. Our DevSecOps services ensure that security is automated and continuous throughout development and operations.
- Penetration Testing: Our penetration testing services involve simulating cyberattacks to identify vulnerabilities in our clients’ systems. We provide detailed reports and remediation plans to strengthen their security posture.
- Security Architecture and Design: We assist in designing and implementing secure IT architectures that align with our clients’ business objectives and regulatory requirements. This includes network design, system architecture, and security controls integration.
Vision and Mission: At Secure Debug Limited, our mission is to utilize the latest technologies and best practices to protect our clients’ digital assets and provide a secure digital environment. Our vision is to become a globally recognized and trusted leader in the cybersecurity field.
Technological Innovations:
- Artificial Intelligence and Machine Learning: We leverage AI and machine learning technologies to optimize our threat detection and incident response processes. These technologies play a critical role in identifying anomalies and automating response procedures.
- Blockchain Technology: We use blockchain technology to ensure the integrity and security of data, providing an additional layer of protection against data breaches and tampering.
- Advanced Encryption Techniques: We employ industry-standard and advanced encryption methods to secure our clients’ data during transmission and storage, ensuring high levels of security.
Contact Information:
Address: 17 Green Lanes, London, England, N16 9BS
Email: [email protected]
Website: www.securedebug.com
Phone: +44 7577 246 156
Our Founder and Leader: Okan YILDIZ, Senior Security Engineer / Software Developer, is the founder and leader of Secure Debug Limited. Okan YILDIZ holds several prestigious certifications, including CASE .NET, CEH, CTIA, ECIH, and CCISO, and possesses extensive expertise in cybersecurity.
References: Secure Debug Limited serves a diverse range of clients across various sectors, including finance, healthcare, energy, and government. Our successful projects and high customer satisfaction rates have established us as a trusted partner in cybersecurity.
At Secure Debug Limited, we continuously innovate and improve to ensure our clients are best protected against cyber threats. Our goal is to maximize security in the digital world, ensuring business continuity and data integrity for our clients.
Stay Connected with Secure Debug
Need expert advice or support from Secure Debug’s cybersecurity consulting and services? We’re here to help. For inquiries, assistance, or to learn more about our offerings, please visit our Contact Us page. Your security is our priority.
Join our professional network on LinkedIn to stay updated with the latest news, insights, and updates from Secure Debug. Follow us here
Post a comment
Secure Debug Limited
Okan YILDIZ
Senior Security Engineer / Software Developer
31.07.2024
Comprehensive Overview of OWASP Software Assurance Maturity Model (SAMM) Version
Introduction to OWASP SAMM v2
The OWASP Software Assurance Maturity Model (SAMM) Version 2 is an evolutionary framework designed to assist organizations in developing, enhancing, and maintaining a robust software security posture. As part of the Open Web Application Security Project (OWASP), SAMM provides a community-driven pathway towards understanding and improving security in software development.
Definition of OWASP SAMM v2
OWASP SAMM v2 is a model that offers a comprehensive and customizable approach to integrating security into software development processes. It is structured around key business functions, which encompass governance, design, implementation, verification, and operations. Each function is broken down into three security practices, making the model both extensive and adaptable to varying organizational needs.
History and Development
Originally launched in 2009, the OWASP SAMM framework was developed to provide an effective and measurable way for organizations to analyze and improve their software security posture. By 2020, rapid advancements in software development practices necessitated an update, leading to the release of Version 2. This update was collaboratively authored by an international group of security experts, and it reflects a comprehensive understanding of modern security challenges. It incorporates feedback from the user community, lessons learned from its practical applications, and aligns with contemporary technologies and methodologies such as DevOps and cloud computing.
Why Use OWASP SAMM v2?
Organizations adopt OWASP SAMM v2 for several strategic reasons:
- Structured Security Strategy: It provides a clear, structured strategy for integrating security into software development, helping organizations address security in a consistent and comprehensive manner.
- Tailored Risk Management: The model is adaptable, allowing organizations to focus on specific practices that best address their unique risks and threat landscape.
- Continuous Improvement: OWASP SAMM v2 encourages a cycle of continuous improvement in security practices through its maturity levels, which guide organizations from initial ad hoc practices to advanced, optimized processes.
- Benchmarking Capabilities: By using the model, organizations can measure their security practices against an established benchmark, facilitating internal assessments and regulatory compliance.
Who Can Use OWASP SAMM v2?
The versatility of OWASP SAMM v2 makes it suitable for a wide array of users:
- Enterprises of All Sizes: From small startups to large enterprises, any organization that develops software can utilize SAMM to better integrate security into their development lifecycles.
- Across Various Industries: Industries such as finance, healthcare, education, and government, where software plays a critical role in operations, find particular value in the structured approach SAMM provides.
- Security Professionals and Consultants: For those tasked with assessing or improving organizational security, SAMM serves as a detailed roadmap and toolkit for enhancing software security maturity.
Implementation Strategy
Implementing OWASP SAMM v2 involves several key steps:
- Initial Self-Assessment: Organizations begin by conducting a baseline assessment to determine their current maturity level across different security practices.
- Goal Setting: Based on the assessment results, specific, measurable goals are set for each practice area, tailored to the organization’s security needs and business objectives.
- Incremental Improvement: Organizations then work on meeting these goals through incremental improvements, systematically addressing each area of the model.
- Regular Review and Adaptation: Regular reviews are conducted to assess progress and adapt the strategy as necessary, ensuring it remains relevant to the changing technology landscape and business requirements.
Conclusion
OWASP SAMM v2 offers a dynamic and strategic framework that helps organizations not just comply with security standards but integrate security as a fundamental component of software development. By following SAMM, organizations can aspire to not only protect their assets and data but also foster a culture of security awareness and resilience.
Functional Areas of OWASP SAMM
Detailed Overview of OWASP SAMM v2 Framework Functional Areas and Security Practices
The OWASP Software Assurance Maturity Model (SAMM) Version 2 is structured around five key functional areas, each divided into specific security practices. These practices are further detailed in two streams per practice, addressing different aspects of security implementation. Here is a breakdown of each functional area and their respective security practices:
1. Governance
Governance focuses on establishing leadership and organizational structures that foster a secure software development culture.
- Strategy & Metrics
- Create & Promote: Developing and promoting a security strategy that aligns with business objectives.
- Measure & Improve: Implementing metrics to measure the effectiveness of security practices and continuously improving them based on these metrics.
- Policy & Compliance
- Policy & Standards: Developing comprehensive security policies and standards that are consistently applied across the organization.
- Compliance Management: Ensuring that all software practices meet internal compliance controls and external regulatory requirements.
- Education & Guidance
- Training & Awareness: Conducting regular security training and awareness programs to enhance employee understanding and engagement with security practices.
- Organization & Culture: Building a security-conscious organizational culture through continuous education and proactive security practices.
2. Design
Design ensures that security is integrated into the software development lifecycle from the earliest stages.
- Threat Assessment
- Application Risk Profile: Creating risk profiles for applications to identify specific security needs.
- Threat Modeling: Systematically modeling potential threats to design robust security measures.
- Security Requirements
- Software Requirements: Defining security requirements that are specific to software functionalities and operational needs.
- Supplier Security: Ensuring that third-party suppliers and partners adhere to security requirements that protect the supply chain.
- Secure Architecture
- Architecture Design: Designing software architectures that inherently prioritize security features and resilience.
- Technology Management: Managing technology stacks to ensure they are updated, secure, and capable of supporting secure applications.
3. Implementation
Implementation covers the development and build processes of software, ensuring secure practices are followed.
- Secure Build
- Build Process: Integrating security into the software build process to ensure consistent application of security practices.
- Software Dependencies: Managing software dependencies to avoid vulnerabilities from third-party components.
- Secure Deployment
- Deployment Process: Ensuring secure deployment practices that maintain the integrity and security of software in production.
- Secret Management: Managing and protecting secrets, such as keys and credentials, to prevent unauthorized access.
- Defect Management
- Defect Tracking: Systematically tracking and managing defects to ensure they are addressed in a timely and secure manner.
- Metrics & Feedback: Using defect metrics and feedback to improve the security of the development process.
4. Verification
Verification ensures that all security measures are properly tested and validated.
- Architecture Assessment
- Architecture Validation: Validating the security of software architectures against defined security standards.
- Architecture Compliance: Ensuring architectures comply with both internal and external security requirements.
- Requirements-driven Testing
- Control Verification: Verifying that security controls meet the intended security requirements and are effective.
- Misuse/Abuse Testing: Testing how the system copes with misuse or malicious actions, ensuring resilience.
- Security Testing
- Scalable Baseline: Developing scalable security testing procedures that can grow with the system.
- Deep Understanding: Gaining a deep understanding of potential vulnerabilities and security challenges through thorough testing.
5. Operations
Operations focus on maintaining and managing software in its operational state to ensure ongoing security.
- Incident Management
- Incident Detection: Developing capabilities to detect security incidents promptly.
- Incident Response: Responding effectively to security incidents to minimize impact and restore normal operations.
- Environment Management
- Configuration Hardening: Hardening configurations to protect against vulnerabilities.
- Patch & Update: Regularly updating and patching systems to protect against known vulnerabilities.
- Operational Management
- Data Protection: Ensuring that data is protected through effective security measures throughout its lifecycle.
- Legacy Management: Managing legacy systems to ensure they remain secure or are phased out in favor of more secure solutions.
Practices Under Each Functional Area
Each functional area within the OWASP SAMM v2 framework includes specific security practices. These practices are designed to be implemented progressively, with the aim of achieving a comprehensive and mature software security posture. Here’s a detailed look at the practices under each functional area:
1. Governance
Governance involves establishing a strategic foundation for security within the organization, aligning it with business goals, and ensuring compliance with relevant standards and regulations.
- Strategy & Metrics
- Create & Promote: Develop a clear security strategy that aligns with organizational objectives and promotes security awareness throughout the organization.
- Measure & Improve: Establish metrics to measure the effectiveness of the security strategy and continuously improve it based on these measurements.
- Policy & Compliance
- Policy & Standards: Formulate and enforce comprehensive security policies and standards that are applicable across the organization.
- Compliance Management: Ensure ongoing compliance with internal policies and external regulatory requirements through regular audits and updates.
- Education & Guidance
- Training & Awareness: Implement continuous security training and awareness programs to educate employees about security best practices.
- Organization & Culture: Foster a security-conscious organizational culture by integrating security principles into everyday business activities and decisions.
2. Design
Design focuses on embedding security into the software development process from the initial stages, ensuring that potential risks are addressed early on.
- Threat Assessment
- Application Risk Profile: Develop risk profiles for applications to identify specific security needs and prioritize risk mitigation efforts.
- Threat Modeling: Conduct systematic threat modeling to identify and address potential threats to the software early in the design phase.
- Security Requirements
- Software Requirements: Define clear and actionable security requirements for software projects, ensuring that security is considered in all aspects of software development.
- Supplier Security: Ensure that third-party suppliers and partners adhere to security requirements that protect the supply chain and maintain overall security integrity.
- Secure Architecture
- Architecture Design: Design software architectures that incorporate robust security controls and are resilient against identified threats.
- Technology Management: Manage and maintain the technology stack to ensure it supports secure application development and deployment.
3. Implementation
Implementation involves ensuring that secure coding and development practices are followed during the software development lifecycle.
- Secure Build
- Build Process: Integrate security into the software build process to ensure that security measures are applied consistently.
- Software Dependencies: Manage software dependencies to prevent vulnerabilities arising from third-party components and libraries.
- Secure Deployment
- Deployment Process: Establish secure deployment processes to maintain the integrity and security of software when it is moved to production environments.
- Secret Management: Implement and maintain robust secret management practices to protect sensitive information such as keys and credentials.
- Defect Management
- Defect Tracking: Systematically track and manage defects to ensure they are addressed promptly and securely.
- Metrics & Feedback: Use metrics and feedback from defect management to continuously improve the security of the software development process.
4. Verification
Verification ensures that all security controls and measures are correctly implemented and effective.
- Architecture Assessment
- Architecture Validation: Regularly validate the security of software architectures against established security standards.
- Architecture Compliance: Ensure that software architectures comply with internal security policies and external regulations.
- Requirements-driven Testing
- Control Verification: Verify that security controls meet the defined security requirements and are effective in mitigating risks.
- Misuse/Abuse Testing: Conduct testing to identify how the system handles misuse or malicious actions, ensuring robustness against such activities.
- Security Testing
- Scalable Baseline: Develop scalable security testing procedures that can adapt as the system grows.
- Deep Understanding: Gain a thorough understanding of potential vulnerabilities through comprehensive and rigorous security testing.
5. Operations
Operations focus on maintaining and enhancing the security of software in the production environment.
- Incident Management
- Incident Detection: Develop capabilities to detect security incidents promptly, minimizing potential damage.
- Incident Response: Establish and maintain an effective incident response process to address and recover from security incidents efficiently.
- Environment Management
- Configuration Hardening: Ensure that the operational environment is securely configured to resist attacks.
- Patch & Update: Regularly patch and update systems to protect against known vulnerabilities.
- Operational Management
- Data Protection: Implement robust data protection measures to safeguard sensitive information throughout its lifecycle.
- Legacy Management: Manage legacy systems to ensure they remain secure or are replaced with more secure alternatives.
How Are Levels Calculated in OWASP SAMM v2?
OWASP SAMM v2 provides a structured approach to assess and improve the maturity of software security practices within an organization. The model defines clear levels and criteria, uses a systematic evaluation process, and employs a scoring system to measure progress. Here’s a detailed look at how levels are calculated and strategies for improvement:
Level Definitions and Criteria
OWASP SAMM v2 defines three maturity levels for each security practice within the framework. These levels indicate the progression from basic, ad-hoc security practices to advanced, optimized processes:
- Level 1 – Initial: At this level, security practices are often informal, reactive, and inconsistently applied across projects. The organization has started to recognize the importance of security, but practices are not standardized.
- Criteria: Basic awareness and ad-hoc implementation of security practices. Initial efforts to address security concerns as they arise.
- Level 2 – Defined: Security practices are documented, repeatable, and consistently applied across similar projects. There is a proactive approach to managing security, and the organization begins to integrate security requirements into the development lifecycle.
- Criteria: Standardized procedures and policies are in place. Security requirements are defined and consistently implemented. There is evidence of proactive risk management.
- Level 3 – Advanced: Security practices are well-defined, optimized, and continuously improved based on metrics and feedback. The organization demonstrates a high level of security maturity with practices integrated deeply into the development lifecycle.
- Criteria: Advanced and automated security practices are implemented. Continuous monitoring, measurement, and improvement of security processes. Demonstrated ability to handle complex security challenges effectively.
Evaluation Process
The evaluation process involves several steps to accurately assess the maturity level of an organization’s security practices:
- Initial Assessment:
- Self-Assessment: Organizations start by conducting a self-assessment to evaluate their current security practices against the SAMM criteria.
- Documentation Review: Collect and review relevant documentation, policies, and procedures related to security practices.
- Gap Analysis:
- Identify gaps between current practices and the desired maturity level.
- Prioritize areas that need improvement based on risk and impact.
- Interviews and Workshops:
- Conduct interviews with key stakeholders, including security teams, developers, and management.
- Facilitate workshops to gather detailed insights and validate self-assessment findings.
- Final Scoring:
- Assign scores based on the evaluation of practices against the SAMM criteria.
- Use these scores to determine the current maturity level for each security practice.
Scoring System
The scoring system in OWASP SAMM v2 provides a quantitative measure of maturity for each security practice. The scoring is based on the following components:
- Practice Coverage: Extent to which security practices are implemented across the organization.
- Consistency: Degree of consistency in applying security practices across different projects and teams.
- Effectiveness: How effective the security practices are in achieving their intended goals and mitigating risks.
Each practice is scored on a scale, typically ranging from 0 (not implemented) to 3 (fully implemented and optimized). The scores are then aggregated to provide an overall maturity level for each functional area.
Strategies for Level Advancement
To advance through the maturity levels, organizations should adopt strategic approaches tailored to their specific needs and current maturity state:
- Resource Allocation:
- Investment in Tools and Training: Allocate resources for security tools, training programs, and skilled personnel.
- Budget for Continuous Improvement: Ensure there is ongoing investment in improving security practices.
- Process Integration:
- Embed Security in the SDLC: Integrate security practices into every stage of the software development lifecycle.
- Standardize Procedures: Develop and enforce standardized security procedures and policies.
- Continuous Improvement:
- Regular Reviews and Audits: Conduct regular reviews and audits of security practices to identify areas for improvement.
- Feedback Loops: Establish feedback loops to continuously refine and enhance security practices based on lessons learned.
- Stakeholder Engagement:
- Involve Key Stakeholders: Engage all relevant stakeholders, including developers, management, and external partners, in the security process.
- Promote a Security Culture: Foster a culture of security awareness and responsibility throughout the organization.
By following these strategies, organizations can systematically enhance their security posture and progress through the maturity levels in OWASP SAMM v2. This approach not only helps in achieving higher security maturity but also ensures that security practices are sustainable and effective in the long term.
Example Scenarios of OWASP SAMM v2 Implementation
Implementing OWASP SAMM v2 can significantly enhance an organization’s software security posture. To illustrate how SAMM can be applied in various contexts, here are detailed example scenarios across different sectors and organizational sizes, along with methods for evaluating and improving existing security levels and sharing success stories.
Different Sector Application Examples
Healthcare Sector
Scenario: A large hospital network seeks to protect patient data and ensure compliance with healthcare regulations like HIPAA.
Implementation Steps:
- Initial Assessment: Conduct a self-assessment using OWASP SAMM to identify current security practices and gaps.
- Governance: Develop a comprehensive security strategy and metrics aligned with HIPAA requirements. Implement policies and compliance management to ensure ongoing adherence to regulations.
- Design: Conduct threat assessments to identify risks specific to patient data systems. Define security requirements for all new software projects.
- Implementation: Implement secure build processes and software dependency management to prevent vulnerabilities.
- Verification: Perform architecture assessments and requirements-driven testing to validate security controls.
- Operations: Establish incident management protocols to detect and respond to security incidents promptly.
Outcome: Enhanced data protection, compliance with HIPAA, and improved ability to respond to security incidents.
Financial Services Sector
Scenario: A multinational bank aims to standardize security practices across its global software development teams.
Implementation Steps:
- Initial Assessment: Use OWASP SAMM to benchmark current security practices across different branches.
- Governance: Create a unified security policy and compliance framework applicable to all branches. Regularly measure and improve security metrics.
- Design: Develop risk profiles for financial applications and incorporate threat modeling.
- Implementation: Standardize secure build processes and enforce secure deployment practices globally.
- Verification: Conduct regular security testing and architecture assessments to ensure compliance with internal standards.
- Operations: Implement robust incident management and environment management practices to maintain security across all operations.
Outcome: Uniform security practices, reduced risk of data breaches, and enhanced regulatory compliance.
Education Sector
Scenario: A university seeks to secure its student information systems and ensure data privacy.
Implementation Steps:
- Initial Assessment: Conduct an assessment to identify existing security measures and gaps.
- Governance: Develop a security strategy that includes policies for data protection and compliance with educational regulations.
- Design: Perform threat assessments and establish security requirements for all software systems handling student data.
- Implementation: Implement secure coding practices and manage software dependencies carefully.
- Verification: Regularly test security controls through architecture validation and requirements-driven testing.
- Operations: Set up incident management processes and ensure continuous patching and updating of systems.
Outcome: Improved protection of student data and compliance with educational privacy regulations.
Scenarios for Small, Medium, and Large Enterprises
Small Business Example
Scenario: A tech startup with limited resources wants to protect its intellectual property and customer data.
Implementation Steps:
- Initial Assessment: Conduct a basic self-assessment to identify critical security gaps.
- Governance: Develop a simple security policy and provide basic security training to all employees.
- Design: Identify key threats and establish minimal security requirements for core applications.
- Implementation: Focus on secure build practices and manage dependencies to avoid common vulnerabilities.
- Verification: Conduct basic security testing and validate critical security controls.
- Operations: Implement a simple incident response plan and regularly update software to fix vulnerabilities.
Outcome: Basic but effective security practices that protect intellectual property and customer data.
Medium-sized Enterprise Example
Scenario: A growing e-commerce company wants to enhance the security of its online platform.
Implementation Steps:
- Initial Assessment: Use OWASP SAMM to assess current security practices and identify improvement areas.
- Governance: Establish comprehensive security policies and provide regular security training to developers and IT staff.
- Design: Perform detailed threat assessments and define security requirements for the e-commerce platform.
- Implementation: Implement secure coding practices and use automated tools for secure builds.
- Verification: Regularly test the platform’s security using advanced security testing techniques.
- Operations: Set up robust incident management and environment management processes to handle security incidents and maintain system security.
Outcome: Improved platform security, better protection against cyber threats, and increased customer trust.
Large Corporation Example
Scenario: A global manufacturer wants to ensure uniform security standards across its diverse software applications.
Implementation Steps:
- Initial Assessment: Conduct a comprehensive assessment of security practices across all global divisions.
- Governance: Develop a global security strategy and ensure all divisions comply with unified security policies.
- Design: Establish risk profiles for critical applications and incorporate threat modeling into the design phase.
- Implementation: Standardize secure build and deployment processes across all divisions.
- Verification: Implement regular security testing and architecture assessments globally.
- Operations: Maintain a centralized incident management system and ensure all systems are regularly patched and updated.
Outcome: Consistent and robust security practices across all divisions, reducing global security risks.
Evaluating and Improving Current Security Levels
Security Evaluation in a Software Development Firm
Scenario: A software development firm wants to evaluate and improve its current security posture.
Evaluation Process:
- Initial Self-Assessment: Conduct a SAMM-based self-assessment to identify current maturity levels across different security practices.
- Gap Analysis: Identify gaps between current practices and desired maturity levels.
- Interviews and Workshops: Gather detailed insights from stakeholders through interviews and workshops.
- Final Scoring: Score each practice based on SAMM criteria to determine the maturity level.
Improvement Strategies:
- Resource Allocation: Invest in security training and tools.
- Process Integration: Integrate security practices into the software development lifecycle.
- Continuous Improvement: Regularly review and update security practices based on feedback and metrics.
- Stakeholder Engagement: Engage all relevant stakeholders to foster a security-aware culture.
Outcome: A comprehensive understanding of current security maturity and a clear roadmap for improvement.
Success Stories and Experience Sharing
Retail Industry Success Story
Scenario: A retail giant successfully integrated OWASP SAMM practices, significantly enhancing their security posture.
Implementation Highlights:
- Governance: Developed a robust security strategy and policies.
- Design: Conducted thorough threat assessments and defined clear security requirements.
- Implementation: Standardized secure coding and deployment practices.
- Verification: Regularly tested security controls and validated architectures.
- Operations: Implemented a comprehensive incident management system.
Results: Significant reduction in data breaches, enhanced customer trust, and improved regulatory compliance.
Technology Firm’s Experience
Scenario: A technology firm shares its experience of implementing OWASP SAMM, focusing on secure architecture and build environments.
Key Learnings:
- Challenges: Initial resistance to change, resource allocation issues, and integrating security into existing workflows.
- Solutions: Conducted regular training, secured executive buy-in, and gradually integrated security practices into development processes.
- Outcomes: Enhanced security posture, reduced vulnerabilities, and a more security-conscious organizational culture.
Sharing Platform: The firm conducted workshops and webinars to share their journey, challenges, and solutions with other organizations, contributing to the wider adoption of SAMM practices.
Outcome: Increased awareness and adoption of OWASP SAMM practices across the industry.
Tables for OWASP SAMM v2 Implementation
Using tables to present information about OWASP SAMM v2 can help in visualizing the framework, assessing maturity levels, and tracking progress. Here are some example tables that you can use in your documentation.
Level and Practices Display Tables
Table 1: Maturity Levels and Key Practices
| Functional Area | Practice | Level 1 (Initial) | Level 2 (Defined) | Level 3 (Advanced) |
| Governance | Strategy & Metrics | Basic strategy awareness | Documented strategy with defined metrics | Continuous improvement with advanced metrics |
| Governance | Policy & Compliance | Ad-hoc policy application | Standardized policies, basic compliance | Full compliance management and automated monitoring |
| Governance | Education & Guidance | Occasional training sessions | Regular training programs and awareness campaigns | Integrated security culture with ongoing education |
| Design | Threat Assessment | Initial risk identification | Comprehensive threat modeling | Continuous threat assessment with real-time updates |
| Design | Security Requirements | Basic security requirements definition | Detailed and documented security requirements | Advanced and adaptive requirements management |
| Design | Secure Architecture | Ad-hoc security controls | Designed secure architecture | Fully integrated and optimized security architecture |
| Implementation | Secure Build | Basic secure build processes | Standardized secure build with automated tools | Advanced build security with continuous integration |
| Implementation | Secure Deployment | Manual secure deployment | Standardized deployment processes | Automated and monitored secure deployment |
| Implementation | Defect Management | Ad-hoc defect tracking | Formal defect tracking process | Advanced defect management with metrics and feedback |
| Verification | Architecture Assessment | Basic architecture review | Standardized architecture validation | Continuous architecture compliance and optimization |
| Verification | Requirements Testing | Initial control verification | Regular control verification | Advanced misuse/abuse testing and continuous testing |
| Verification | Security Testing | Basic security testing | Comprehensive security testing | Advanced security testing with deep vulnerability analysis |
| Operations | Incident Management | Basic incident response | Formal incident detection and response | Advanced incident management with continuous improvement |
| Operations | Environment Management | Initial configuration hardening | Standardized patch and update processes | Continuous environment management and optimization |
| Operations | Operational Management | Basic data protection | Standardized data and legacy management | Advanced operational management with data security integration |
Assessment Results Table
Table 2: Security Assessment Results
| Practice | Current Level | Findings | Recommendations |
| Strategy & Metrics | 1 | Lack of documented security strategy | Develop and document a comprehensive strategy |
| Policy & Compliance | 2 | Policies are in place but compliance is inconsistent | Implement regular compliance audits |
| Education & Guidance | 1 | Irregular training sessions | Establish a regular training program |
| Threat Assessment | 2 | Basic threat modeling exists | Enhance threat modeling with real-time updates |
| Security Requirements | 1 | Basic requirements defined | Develop detailed security requirements |
| Secure Architecture | 2 | Architecture design includes security controls | Optimize architecture with advanced controls |
| Secure Build | 1 | Basic secure build processes | Implement automated secure build tools |
| Secure Deployment | 1 | Manual deployment processes | Standardize and automate deployment processes |
| Defect Management | 2 | Formal defect tracking in place | Use metrics for continuous improvement |
| Architecture Assessment | 2 | Standard architecture validation | Regularly update validation processes |
| Requirements Testing | 1 | Initial control verification | Implement comprehensive control testing |
| Security Testing | 1 | Basic testing procedures | Develop advanced security testing protocols |
| Incident Management | 2 | Formal incident response but lacks continuous improvement | Implement continuous improvement processes |
| Environment Management | 2 | Standard patch and update processes | Optimize environment management practices |
| Operational Management | 1 | Basic data protection measures | Develop advanced data security protocols |
Progress Tracking and Reporting Tables
Table 3: Progress Tracking Table
| Date | Practice | Current Level | Target Level | Status | Next Steps |
| 2024-08-01 | Secure Build | 1 | 2 | In Progress | Implement automated build tools |
| 2024-08-01 | Security Testing | 2 | 3 | On Schedule | Develop advanced testing protocols |
| 2024-08-01 | Incident Management | 1 | 2 | Behind | Establish formal incident response plan |
| 2024-08-01 | Policy & Compliance | 2 | 3 | In Progress | Conduct regular compliance audits |
| 2024-08-01 | Education & Guidance | 1 | 2 | In Progress | Develop a regular security training program |
Annual Security Report Table
Table 4: Annual Security Report Table
| Year | Functional Area | Improvements Achieved | Outstanding Issues | Compliance Status |
| 2023 | Governance | Developed security strategy and metrics | Consistency in compliance enforcement | Compliant with major regulations |
| 2023 | Design | Implemented comprehensive threat modeling | Enhancing security requirements | Compliant |
| 2023 | Implementation | Standardized secure build process | Automating deployment processes | Partially Compliant |
| 2023 | Verification | Regular control verification | Advanced misuse/abuse testing | Compliant |
| 2023 | Operations | Formalized incident management process | Continuous improvement in incident response | Compliant |
Conclusion
At Secure Debug, we understand that in today’s rapidly evolving digital landscape, robust software security is more crucial than ever. Implementing a structured and comprehensive framework like OWASP SAMM v2 is essential for organizations seeking to protect their digital assets, ensure compliance, and build trust with their customers.
OWASP SAMM v2 offers a clear roadmap for assessing, improving, and measuring the maturity of your software security practices. By systematically addressing security across governance, design, implementation, verification, and operations, this model helps organizations to not only identify and mitigate risks but also to embed security into their core business processes.
Our team of experienced consultants at Secure Debug is dedicated to guiding you through each step of this journey. We offer tailored assessments, strategic planning, and hands-on support to help you achieve higher maturity levels in your security practices. Whether you are a small startup or a large enterprise, our services are designed to meet your unique needs and challenges.
By partnering with Secure Debug, you gain access to:
- Expert Knowledge: Our consultants bring deep expertise in OWASP SAMM and other leading security frameworks.
- Customized Solutions: We develop security strategies that align with your business goals and industry requirements.
- Continuous Improvement: We help you establish continuous improvement processes to keep your security posture up-to-date with evolving threats.
Investing in a structured security framework like OWASP SAMM v2 is not just about compliance—it’s about safeguarding your business’s future. With Secure Debug by your side, you can confidently navigate the complexities of software security, ensuring your systems are resilient, your data is protected, and your customers’ trust is maintained.
Let us help you turn security challenges into strengths. Contact Secure Debug today to learn more about how we can support your journey towards a more secure and mature software development lifecycle.
About Secure Debug Limited
Company Profile: Secure Debug Limited is a London-based cybersecurity services firm specializing in providing advanced security solutions to protect critical infrastructure and sensitive data. Our mission is to offer a secure digital environment for our clients by safeguarding their assets from cyber threats.
Our Services:
- Threat Assessment and Vulnerability Management: We conduct comprehensive analyses of our clients’ current security postures to identify potential threats and vulnerabilities. These assessments help organizations close security gaps and enhance their defense strategies.
- Incident Response and Recovery: In the event of a cyberattack, we provide rapid and effective response services to minimize damage and restore operations as quickly as possible. Post-incident analyses also help prepare for future threats.
- Continuous Monitoring and Security Operations: Our 24/7 monitoring services ensure that our clients’ networks are constantly overseen, detecting any anomalies. Our Security Operations Center (SOC) proactively takes measures against potential threats.
- Compliance and Regulatory Requirements: We assist our clients in achieving compliance with sector-specific and legal regulations, including GDPR, PCI-DSS, and ISO 27001, among others.
- Application Security: We provide robust application security services to ensure that our clients’ software is secure throughout its lifecycle. This includes code reviews, secure coding practices, and application security testing.
- DevSecOps: We integrate security practices into every phase of the software development lifecycle, fostering a culture where security is a shared responsibility. Our DevSecOps services ensure that security is automated and continuous throughout development and operations.
- Penetration Testing: Our penetration testing services involve simulating cyberattacks to identify vulnerabilities in our clients’ systems. We provide detailed reports and remediation plans to strengthen their security posture.
- Security Architecture and Design: We assist in designing and implementing secure IT architectures that align with our clients’ business objectives and regulatory requirements. This includes network design, system architecture, and security controls integration.
Vision and Mission: At Secure Debug Limited, our mission is to utilize the latest technologies and best practices to protect our clients’ digital assets and provide a secure digital environment. Our vision is to become a globally recognized and trusted leader in the cybersecurity field.
Technological Innovations:
- Artificial Intelligence and Machine Learning: We leverage AI and machine learning technologies to optimize our threat detection and incident response processes. These technologies play a critical role in identifying anomalies and automating response procedures.
- Blockchain Technology: We use blockchain technology to ensure the integrity and security of data, providing an additional layer of protection against data breaches and tampering.
- Advanced Encryption Techniques: We employ industry-standard and advanced encryption methods to secure our clients’ data during transmission and storage, ensuring high levels of security.
Contact Information:
Address: 17 Green Lanes, London, England, N16 9BS
Email: [email protected]
Website: www.securedebug.com
Phone: +44 7577 246 156
Our Founder and Leader: Okan YILDIZ, Senior Security Engineer / Software Developer, is the founder and leader of Secure Debug Limited. Okan YILDIZ holds several prestigious certifications, including CASE .NET, CEH, CTIA, ECIH, and CCISO, and possesses extensive expertise in cybersecurity.
References: Secure Debug Limited serves a diverse range of clients across various sectors, including finance, healthcare, energy, and government. Our successful projects and high customer satisfaction rates have established us as a trusted partner in cybersecurity.
At Secure Debug Limited, we continuously innovate and improve to ensure our clients are best protected against cyber threats. Our goal is to maximize security in the digital world, ensuring business continuity and data integrity for our clients.
Stay Connected with Secure Debug
Need expert advice or support from Secure Debug’s cybersecurity consulting and services? We’re here to help. For inquiries, assistance, or to learn more about our offerings, please visit our Contact Us page. Your security is our priority.
Join our professional network on LinkedIn to stay updated with the latest news, insights, and updates from Secure Debug. Follow us here







