In-Depth Exploration of IDOR: A Comprehensive Guide to Understanding, Detecting, and Preventing Insecure Direct Object Reference Vulnerabilities
Introduction
Insecure Direct Object Reference (IDOR) vulnerabilities are a significant threat to web applications, putting sensitive data and critical functionality at risk. To help safeguard your organization, this blog post offers a deep dive into the details of IDOR vulnerabilities, exploring real-world examples, effective detection methods, and providing robust prevention strategies complete with code samples.
Understanding Insecure Direct Object Reference (IDOR)
IDOR vulnerabilities occur when a web application exposes direct access to internal objects or resources using user-supplied input. Without proper access control mechanisms, attackers can manipulate the input, allowing them unauthorized access to sensitive data or functionality.
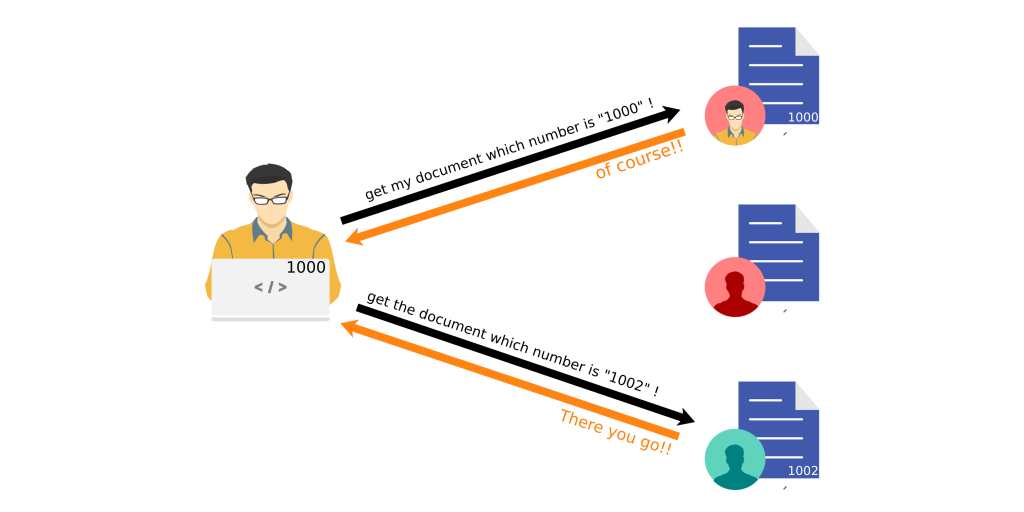
Case Study: Exposing Private Documents
Imagine a file storage application that uses sequential numeric IDs to identify files. When a user accesses their files, the application generates a URL like “https://filestorage.com/viewfile?fileid=1001.” An attacker could exploit this by incrementing or decrementing the “fileid” parameter to view unauthorized files, potentially revealing private documents or sensitive data.
Detecting IDOR Vulnerabilities
Automated scanners may not effectively detect IDOR vulnerabilities, as they require an understanding of the application’s logic and access controls. Manual testing, often using a combination of proxy tools like Burp Suite and manual input manipulation, is typically more successful in identifying IDOR vulnerabilities.
Preventing IDOR Vulnerabilities
- Robust Access Controls: Implement server-side checks to verify user permissions before granting access to sensitive resources or actions.
Example using Python and Flask:
@app.route('/viewfile')
@login_required
def view_file():
file_id = request.args.get('fileid')
file = File.query.get(file_id)
if file and file.owner_id == current_user.id:
return send_file(file.path)
else:
abort(403)
- Indirect Object References: Replace direct references to internal objects (e.g., database IDs) with indirect references (e.g., randomly generated tokens). Map these indirect references to the actual objects server-side, preventing unauthorized manipulation.
Example using Python and Flask:
import uuid
def generate_file_token():
return uuid.uuid4().hex
def get_file_by_token(token):
return File.query.filter_by(token=token).first()
@app.route('/viewfile')
@login_required
def view_file():
file_token = request.args.get('filetoken')
file = get_file_by_token(file_token)
if file and file.owner_id == current_user.id:
return send_file(file.path)
else:
abort(403)
- User Input Validation: Rigorously validate user-supplied input to restrict unauthorized access attempts. Employ both client-side and server-side validation, but prioritize server-side checks, as client-side validation can be bypassed.
Example using Python and Flask:
from wtforms import StringField, IntegerField, validators
class FileRequestForm(FlaskForm):
file_id = IntegerField('File ID', [validators.DataRequired(), validators.NumberRange(min=1)])
@app.route('/viewfile', methods=['GET', 'POST'])
@login_required
def view_file():
form = FileRequestForm(request.form)
if request.method == 'POST' and form.validate():
file_id = form.file_id.data
file = File.query.get(file_id)
if file and file.owner_id == current_user.id:
return send_file(file.path)
else:
abort(403)
else:
return render_template('viewfile.html', form=form)
- Least Privilege Principle: Grant users the minimum level of access necessary to perform their tasks. This approach limits the potential damage caused by IDOR vulnerabilities.
- Logging and Monitoring: Regularly log and monitor user access to sensitive resources. This practice aids in the early detection of IDOR attacks and supports incident response efforts.
Example using Python and Flask:
import logging
def log_access_attempt(user_id, resource_id, success):
logging.info(f"User {user_id} attempted to access resource {resource_id}. Access {'granted' if success else 'denied'}.")
@app.route('/viewfile')
@login_required
def view_file():
file_id = request.args.get('fileid')
file = File.query.get(file_id)
if file and file.owner_id == current_user.id:
log_access_attempt(current_user.id, file_id, True)
return send_file(file.path)
else:
log_access_attempt(current_user.id, file_id, False)
abort(403)
Conclusion
Understanding, detecting, and mitigating IDOR vulnerabilities is crucial for maintaining strong web application security. By implementing the preventative measures and incorporating code samples outlined in this blog post, you can significantly reduce the risk of unauthorized access and protect your organization’s sensitive data.







