Mastering DAST vs. SAST: An Ultra-Extensive Guide to Application Security Testing
Modern applications—encompassing web platforms, APIs, and mobile solutions—demand rigorous security testing to detect and prevent vulnerabilities. Two prominent methodologies, Dynamic Application Security Testing (DAST) and Static Application Security Testing (SAST), serve as critical pillars of DevSecOps and secure SDLC practices. While both aim to identify security flaws, they approach the challenge from distinct angles: SAST…
Read morePOSTED BY
Secure Debug
Mastering Secure SDLC: An In-Depth Guide to Integrating Security into the Secure Software Development Life Cycle
In the ever-evolving landscape of cybersecurity, integrating security into the Secure Software Development Life Cycle (SDLC) is no longer optional—it’s imperative. As cyber threats become more sophisticated, ensuring that security measures are embedded at every phase of software development is crucial. This comprehensive guide delves deep into Secure SDLC practices, providing insights, methodologies, tools, and…
Read morePOSTED BY
Secure Debug
Fortifying Your Applications: An Exhaustive Guide to Defending Against Remote Code Execution (RCE) Attacks with Code Examples
Remote Code Execution (RCE) stands as one of the most perilous vulnerabilities in the cybersecurity landscape. It empowers attackers to execute arbitrary code on a target system, potentially leading to complete system compromise. This extensive guide delves deep into RCE, elucidating its mechanisms, real-world examples, detection methods, and, crucially, defense strategies enriched with code examples to…
Read morePOSTED BY
Secure Debug
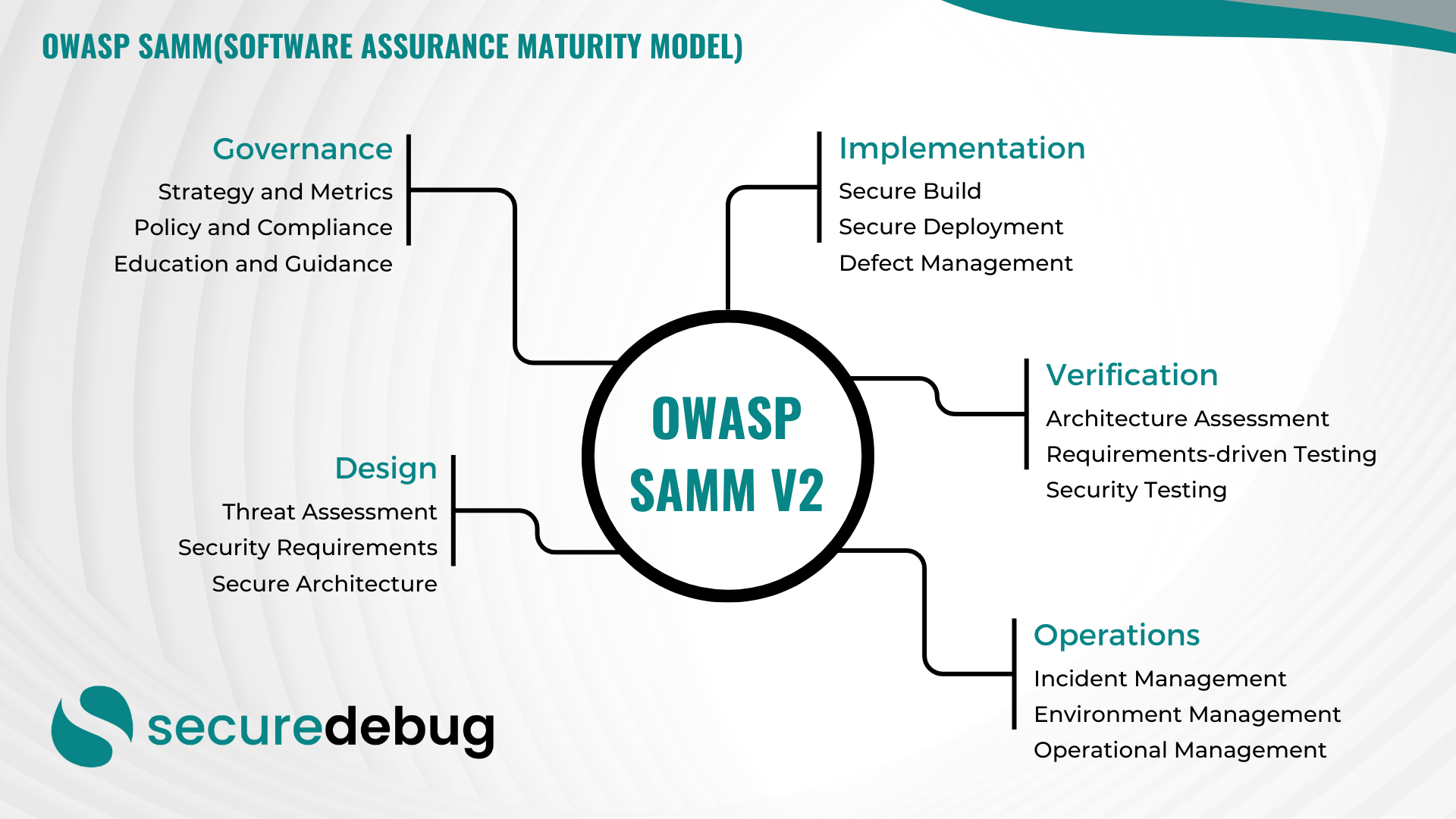
Comprehensive Guide to Implementing OWASP SAMM v2
Comprehensive Overview of OWASP Software Assurance Maturity Model (SAMM) Version 2 Introduction to OWASP SAMM v2 The OWASP Software Assurance Maturity Model (SAMM) Version 2 is an evolutionary framework designed to assist organizations in developing, enhancing, and maintaining a robust software security posture. As part of the Open Web Application Security Project (OWASP), SAMM provides…
Read morePOSTED BY
Secure Debug
Securing Applications Against SQL Injection Vulnerabilities
Securing Applications Against SQL Injection Vulnerabilities SQL injection attacks have been a persistent threat to web applications, allowing malicious actors to manipulate databases and access sensitive information. As a cybersecurity firm, it is crucial to understand the importance of securing applications against SQL injection vulnerabilities to protect data integrity and user privacy. Understanding SQL Injection…
Read morePOSTED BY
Okan YILDIZ
Cybersecurity for Virtual Reality (VR)
Cybersecurity for Virtual Reality (VR) Virtual Reality (VR) has revolutionized the way we experience digital content, offering immersive and interactive environments. However, this exciting technology also brings new cybersecurity challenges that need to be addressed to ensure user safety and protect sensitive data. One of the key aspects of cybersecurity for VR is protecting user…
Read morePOSTED BY
Okan YILDIZ
The Importance of Firewalls in Ensuring Network Security
The Importance of Firewalls in Ensuring Network Security Firewalls play a crucial role in safeguarding your network security from potential cyber threats. As a cybersecurity firm, Secure Debug understands the significance of implementing strong firewall protection to prevent unauthorized access and protect sensitive information. In this blog post, we will delve into the world of…
Read morePOSTED BY
Okan YILDIZ
Secure Code Review Practices
Secure Code Review Practices At Secure Debug, we understand the critical importance of secure code in maintaining robust cybersecurity measures. Secure code review is a fundamental practice that helps identify vulnerabilities and weaknesses in software applications. In this blog post, we will explore the best practices for conducting secure code reviews and how they contribute…
Read morePOSTED BY
Okan YILDIZ
Enhancing Cybersecurity with Burp Suite, DevSecOps, SAST, and DAST
Enhancing Cybersecurity with Burp Suite, DevSecOps, SAST, and DAST Welcome to the Secure Debug blog! In this post, we will explore the powerful tools and practices that can significantly enhance your cybersecurity efforts. We’ll delve into the world of Burp Suite, DevSecOps, SAST (Static Application Security Testing), and DAST (Dynamic Application Security Testing) to understand…
Read morePOSTED BY
Okan YILDIZ
The Importance of Application Security in Today’s Digital Landscape
The Importance of Application Security in Today’s Digital Landscape As technology continues to advance at a rapid pace, applications have become an integral part of our daily lives. From mobile apps to web-based software, we rely on these applications for various tasks and transactions. However, with the increasing reliance on applications, there is also a…
Read morePOSTED BY