Mastering Third-Party Risk Management: A Comprehensive Guide to Mitigating Supply Chain Threats
As organizations become more interconnected and reliant on external vendors, suppliers, and service providers, the potential risk associated with third-party relationships has risen significantly. A data breach, regulatory violation, or operational disruption in a third-party vendor’s environment can swiftly propagate through the supply chain, impacting business continuity, brand reputation, and regulatory compliance. Robust third-party risk…
Read morePOSTED BY
Secure Debug
Mastering Secure SDLC: An In-Depth Guide to Integrating Security into the Secure Software Development Life Cycle
In the ever-evolving landscape of cybersecurity, integrating security into the Secure Software Development Life Cycle (SDLC) is no longer optional—it’s imperative. As cyber threats become more sophisticated, ensuring that security measures are embedded at every phase of software development is crucial. This comprehensive guide delves deep into Secure SDLC practices, providing insights, methodologies, tools, and…
Read morePOSTED BY
Secure Debug
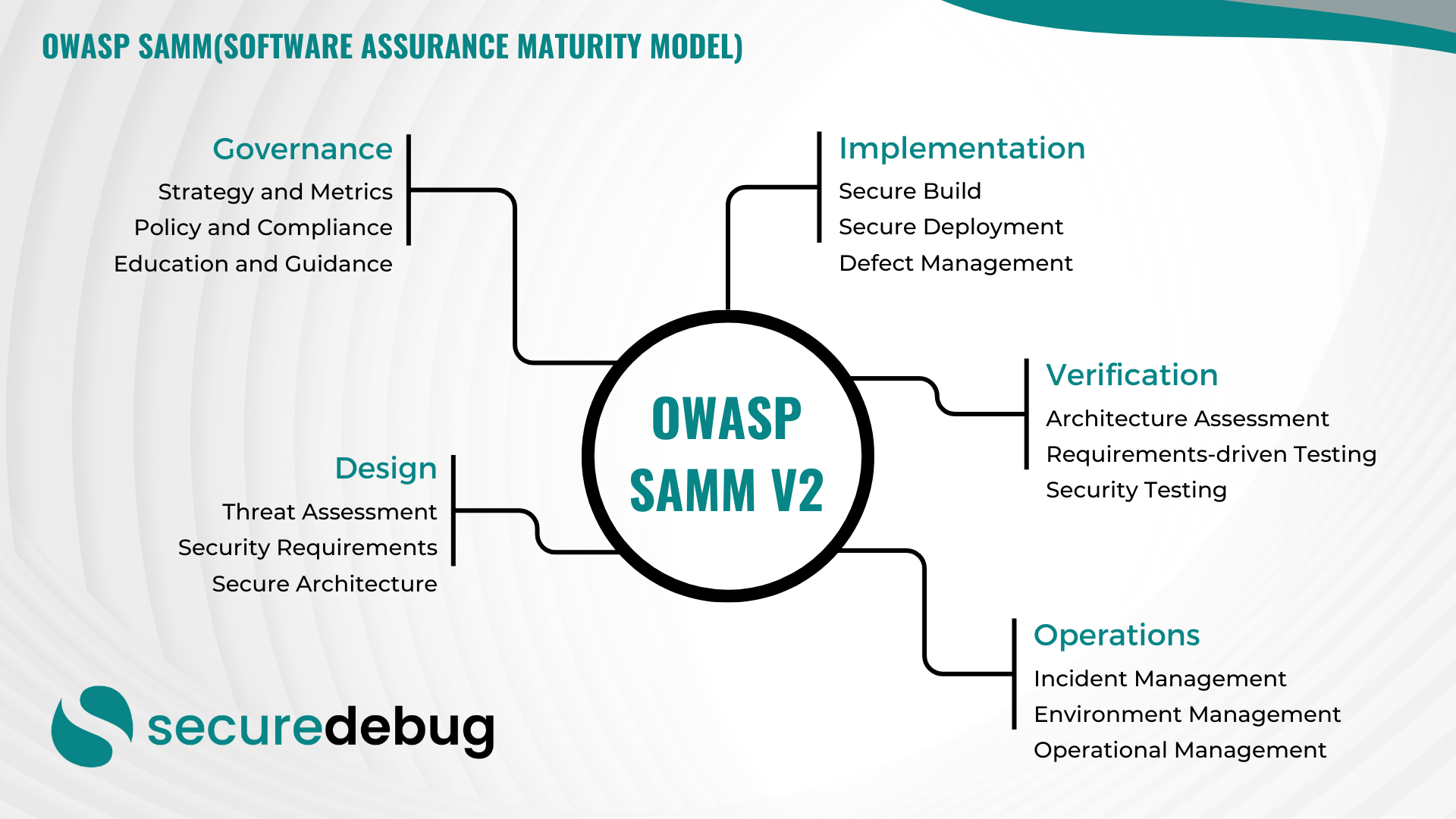
Comprehensive Guide to Implementing OWASP SAMM v2
Comprehensive Overview of OWASP Software Assurance Maturity Model (SAMM) Version 2 Introduction to OWASP SAMM v2 The OWASP Software Assurance Maturity Model (SAMM) Version 2 is an evolutionary framework designed to assist organizations in developing, enhancing, and maintaining a robust software security posture. As part of the Open Web Application Security Project (OWASP), SAMM provides…
Read morePOSTED BY
Secure Debug
Navigating Data Sovereignty Compliance: A Comprehensive Guide for Businesses
Understanding The Compliance Data sovereignty compliance refers to the legal requirements that dictate where data is stored and how it is managed. In today’s digital age, businesses must adhere to these regulations to protect sensitive information and maintain trust with their customers. Key Considerations for The Sovereignty Compliance When it comes to sovereignty compliance, there…
Read morePOSTED BY
Okan YILDIZ
Protecting Financial Transactions: A Deep Dive into Cybersecurity in FinTech
The Rise of FinTech and Cybersecurity Challenges In recent years, the financial technology (FinTech) industry has experienced exponential growth, revolutionizing the way we conduct financial transactions. From mobile banking apps to online payment platforms, FinTech companies have made financial services more accessible and convenient. However, this rapid digital transformation has also exposed the industry to…
Read morePOSTED BY
Okan YILDIZ
The Power of Security Information and Event Management (SIEM)
The Power of Security Information and Event Management (SIEM) As cyber threats continue to evolve and become more sophisticated, organizations must strengthen their cybersecurity posture to protect their sensitive data and systems. One crucial tool in this arsenal is Security Information and Event Management (SIEM). SIEM is a comprehensive approach to security management that enables…
Read morePOSTED BY
Okan YILDIZ
Enhancing Email Gateway Security: Protecting Your Business from Cyber Threats
Enhancing Email Gateway Security: Protecting Your Business from Cyber Threats In today’s digital landscape, email remains a primary communication channel for businesses. However, it is also a common target for cybercriminals seeking to exploit vulnerabilities and gain unauthorized access to sensitive information. To safeguard your organization from email-based threats, implementing robust email gateway security measures…
Read morePOSTED BY
Okan YILDIZ
The Importance of Cybersecurity Whitepapers in Today’s Digital Landscape
The Importance of Cybersecurity Whitepapers in Today’s Digital Landscape In the rapidly evolving world of cybersecurity, staying ahead of the curve is essential. As threats become more sophisticated, organizations need to arm themselves with the latest knowledge and insights to protect their sensitive data and systems. This is where cybersecurity whitepapers come into play. A…
Read morePOSTED BY
Okan YILDIZ
GDPR Compliance: Safeguarding Data in the Digital Age
GDPR Compliance: Safeguarding Data in the Digital Age In today’s interconnected world, data privacy and protection have become paramount. With the rise in cyber threats and data breaches, organizations must prioritize compliance with regulations to ensure the safety and security of their customers’ personal information. One such regulation that has had a significant impact on…
Read morePOSTED BY
Okan YILDIZ
Understanding Cybersecurity Standards
Introduction Welcome to Secure Debug’s blog post on cybersecurity standards. In today’s digital age, cybersecurity is of paramount importance to protect sensitive information and prevent unauthorized access to networks and systems. Cybersecurity standards play a crucial role in establishing a framework for organizations to follow in order to ensure the security of their data and…
Read morePOSTED BY