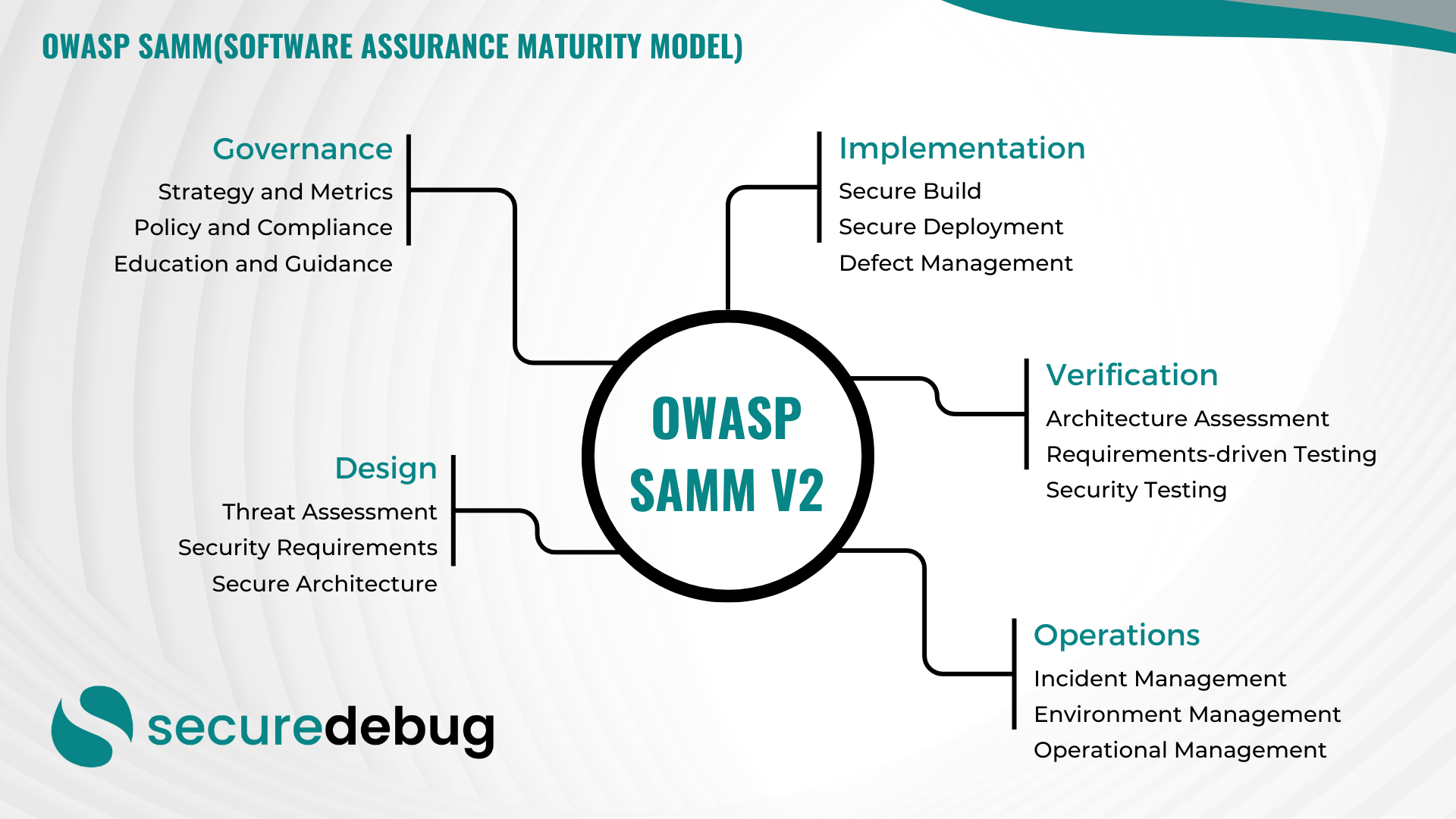
Comprehensive Guide to Implementing OWASP SAMM v2
Comprehensive Overview of OWASP Software Assurance Maturity Model (SAMM) Version 2 Introduction to OWASP SAMM v2 The OWASP Software Assurance Maturity Model (SAMM) Version 2 is an evolutionary framework designed to assist organizations in developing, enhancing, and maintaining a robust software security posture. As part of the Open Web Application Security Project (OWASP), SAMM provides…
Read morePOSTED BY
Secure Debug
Third-Party Risk Management: Safeguarding Your Business in a Connected World
Welcome to the Secure Debug blog! In today’s digital landscape, businesses rely heavily on third-party vendors and partners to streamline operations, enhance productivity, and deliver quality services. However, with increased reliance on external entities comes an inherent risk – third-party vulnerabilities can expose your organization to potential cyber threats. This is where Third-Party Risk Management…
Read morePOSTED BY
Okan YILDIZ
Attack Surface Reduction: Strengthening Your Cybersecurity Defenses
Attack Surface Reduction: Strengthening Your Cybersecurity Defenses As the digital landscape continues to evolve, the threat landscape for organizations also grows. Cyberattacks have become more sophisticated, making it crucial for businesses to take proactive measures to protect their valuable assets. One effective strategy is attack surface reduction, which aims to minimize an organization’s potential vulnerabilities…
Read morePOSTED BY
Okan YILDIZ
Blue Teaming: A Comprehensive and In-Depth Guide to Boost Your Business’s Cybersecurity
Introduction The digital age has made cybersecurity a top priority for businesses of all sizes. With cyber threats constantly evolving, it is crucial for organizations to adopt comprehensive strategies to protect their data and assets. While red teaming is a well-known concept, blue teaming plays an equally vital role in maintaining a strong cybersecurity posture.…
Read morePOSTED BY