Comprehensive Guide to Implementing OWASP SAMM v2
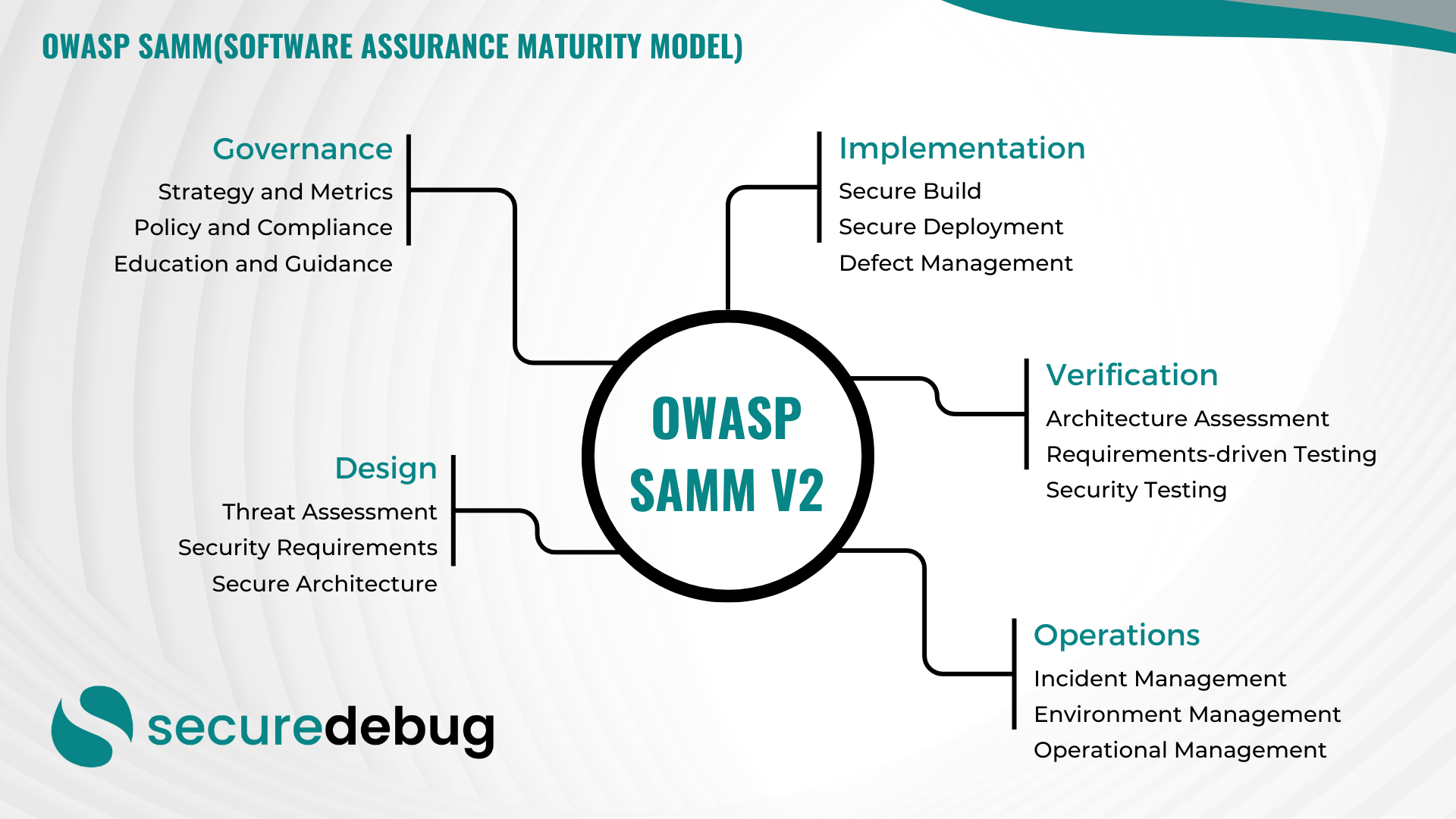
Comprehensive Overview of OWASP Software Assurance Maturity Model (SAMM) Version 2 Introduction to OWASP SAMM v2 The OWASP Software Assurance Maturity Model (SAMM) Version 2 is an evolutionary framework designed to assist organizations in developing, enhancing, and maintaining a robust software security posture. As part of the Open Web Application Security Project (OWASP), SAMM provides…
Read morePOSTED BY
Secure Debug
Exploring the Role of Cybersecurity Metrics in Protecting Your Organization
Exploring the Role of Cybersecurity Metrics in Protecting Your Organization As the threat landscape continues to evolve, it is crucial for organizations to adopt proactive measures to protect their valuable assets and sensitive data. One of the key components of a robust cybersecurity strategy is the use of cybersecurity metrics. In this blog post, we…
Read morePOSTED BY
Okan YILDIZ
Understanding Cyber Risk Quantification: A Comprehensive Guide
Introduction Welcome to Secure Debug’s cybersecurity blog! In this post, we will delve into the fascinating world of Cyber Risk Quantification (CRQ). As organizations continue to face increasing cyber threats, understanding and quantifying the potential risks becomes paramount. CRQ provides a systematic approach to measure and assess these risks, enabling businesses to make informed decisions…
Read morePOSTED BY
Okan YILDIZ
Protecting Your Organization with Threat Intelligence
Protecting Your Organization with Threat Intelligence In today’s rapidly evolving digital landscape, organizations face an increasing number of sophisticated cyber threats. To stay one step ahead of attackers, it is crucial for businesses to adopt proactive security measures. One such measure is leveraging the power of threat intelligence. Threat intelligence refers to the knowledge and…
Read morePOSTED BY
Okan YILDIZ
Understanding Cybersecurity Standards
Introduction Welcome to Secure Debug’s blog post on cybersecurity standards. In today’s digital age, cybersecurity is of paramount importance to protect sensitive information and prevent unauthorized access to networks and systems. Cybersecurity standards play a crucial role in establishing a framework for organizations to follow in order to ensure the security of their data and…
Read morePOSTED BY