Mastering Secure Coding in Java: A Comprehensive Guide
Java, renowned for its platform independence, robustness, and extensive ecosystem, powers a wide array of applications—from enterprise solutions and web services to Android mobile apps and IoT devices. However, as the prevalence of Java applications increases, so does the incentive for attackers to exploit security weaknesses. Ensuring secure coding practices in Java from the ground…
Read morePOSTED BY
Secure Debug
Mastering Secure SDLC: An In-Depth Guide to Integrating Security into the Secure Software Development Life Cycle
In the ever-evolving landscape of cybersecurity, integrating security into the Secure Software Development Life Cycle (SDLC) is no longer optional—it’s imperative. As cyber threats become more sophisticated, ensuring that security measures are embedded at every phase of software development is crucial. This comprehensive guide delves deep into Secure SDLC practices, providing insights, methodologies, tools, and…
Read morePOSTED BY
Secure Debug
Fortifying Your Applications: An Exhaustive Guide to Defending Against Remote Code Execution (RCE) Attacks with Code Examples
Remote Code Execution (RCE) stands as one of the most perilous vulnerabilities in the cybersecurity landscape. It empowers attackers to execute arbitrary code on a target system, potentially leading to complete system compromise. This extensive guide delves deep into RCE, elucidating its mechanisms, real-world examples, detection methods, and, crucially, defense strategies enriched with code examples to…
Read morePOSTED BY
Secure Debug
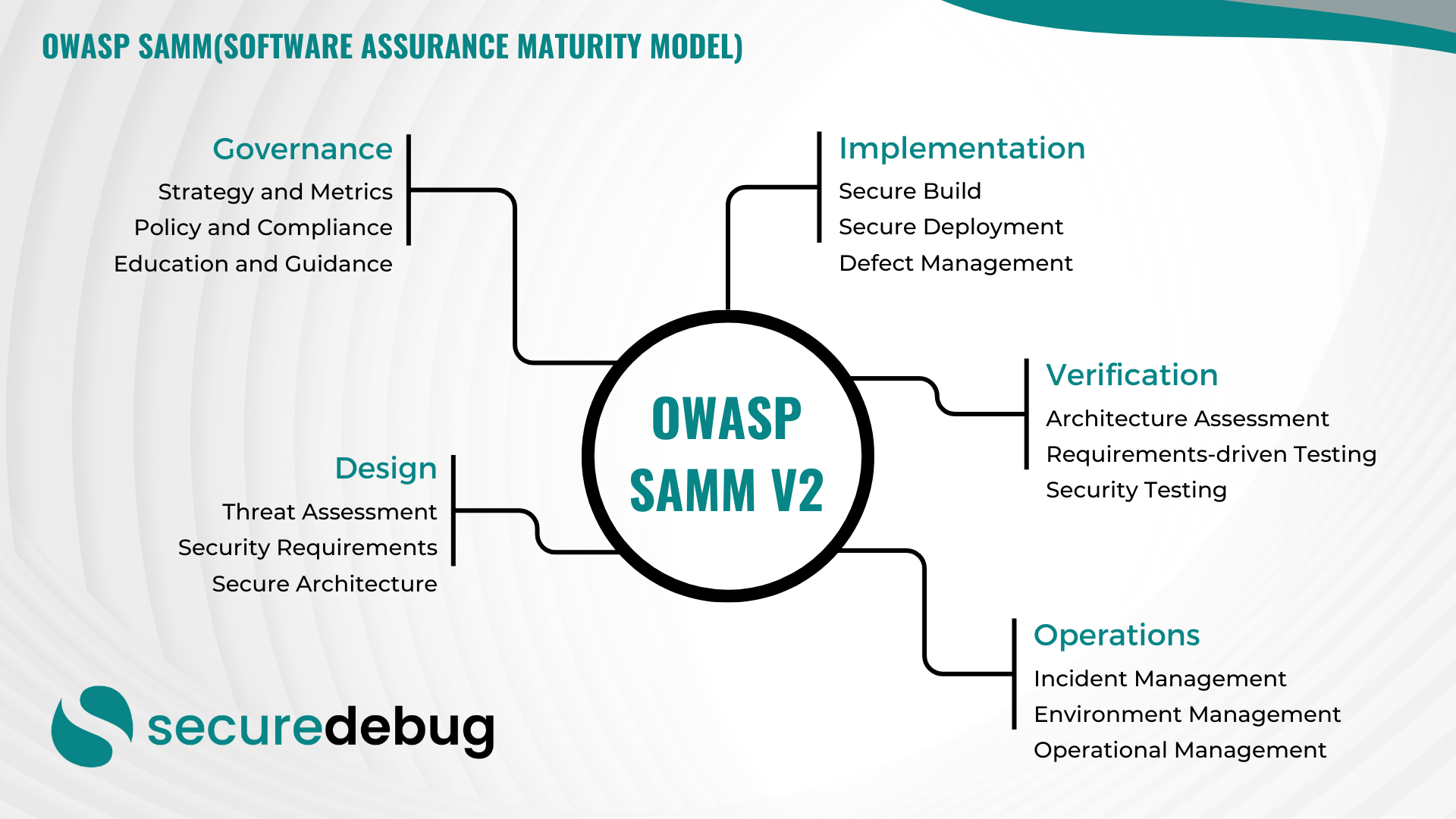
Comprehensive Guide to Implementing OWASP SAMM v2
Comprehensive Overview of OWASP Software Assurance Maturity Model (SAMM) Version 2 Introduction to OWASP SAMM v2 The OWASP Software Assurance Maturity Model (SAMM) Version 2 is an evolutionary framework designed to assist organizations in developing, enhancing, and maintaining a robust software security posture. As part of the Open Web Application Security Project (OWASP), SAMM provides…
Read morePOSTED BY
Secure Debug
Secure Coding Practices in Python
Secure Coding Practices in Python Python is a powerful and versatile programming language used by developers worldwide. However, with great power comes great responsibility. In today’s digital age, cybersecurity threats are on the rise, making it crucial for developers to follow secure coding practices to protect their applications from potential vulnerabilities. Here are some essential…
Read morePOSTED BY
Okan YILDIZ
Effective Remote Code Execution (RCE) Defense Strategies
Introduction Remote Code Execution (RCE) is a critical vulnerability that can allow attackers to gain unauthorized access to a system, execute arbitrary code, and potentially take complete control. To defend against RCE attacks, organizations must adopt robust defense strategies that mitigate these risks effectively. Understanding Remote Code Execution Before delving into defense strategies, it is…
Read morePOSTED BY
Okan YILDIZ
The Importance of Application Security in Today’s Digital Landscape
The Importance of Application Security in Today’s Digital Landscape As technology continues to advance at a rapid pace, applications have become an integral part of our daily lives. From mobile apps to web-based software, we rely on these applications for various tasks and transactions. However, with the increasing reliance on applications, there is also a…
Read morePOSTED BY
Okan YILDIZ
Implementing DevSecOps for Enhanced Cybersecurity
Introduction DevSecOps, a combination of Development, Security, and Operations, is an approach that emphasizes integrating security practices throughout the software development lifecycle. By adopting DevSecOps, organizations can proactively address cybersecurity threats and vulnerabilities from the early stages of development. Benefits of DevSecOps 1. Early Vulnerability Detection: DevSecOps allows for continuous monitoring and testing of code,…
Read morePOSTED BY
Okan YILDIZ
The Importance of Application Security in Today’s Digital Landscape
The Importance of Application Security in Today’s Digital Landscape In an era dominated by digital technologies and the widespread use of applications, ensuring robust application security has become a critical necessity for organizations. With the increasing number of cyber threats and the potential for devastating data breaches, investing in application security is no longer optional…
Read morePOSTED BY
Okan YILDIZ
Understanding the Importance of Secure Coding in Cybersecurity
In today’s digital world, coding has become the backbone of all technological advancements. However, the rise in technological innovations has also led to an increase in the vulnerabilities that hackers can exploit. This is where the importance of secure coding in cybersecurity comes into play. Secure coding is the practice of writing codes in a…
Read morePOSTED BY