Mastering Medical Device Cybersecurity: An Exhaustive Guide to Safeguarding Patient Safety and Data Integrity
As healthcare increasingly relies on connected medical devices—ranging from implantable insulin pumps and pacemakers to infusion pumps, MRI scanners, and surgical robots—the importance of cybersecurity intensifies. A single vulnerability in a device can compromise patient safety, disrupt critical procedures, and lead to regulatory and reputational damage. Ensuring robust cybersecurity in medical devices is not only…
Read morePOSTED BY
Secure Debug
Mastering Penetration Testing Methodology: A Comprehensive Guide
Penetration testing (pentesting) is an essential exercise in assessing the security posture of an organization’s systems, networks, and applications. By simulating adversarial behavior, pentesters uncover vulnerabilities and weaknesses before malicious actors can exploit them. A well-structured methodology ensures that tests are thorough, ethical, reproducible, and effective at driving meaningful improvements in security. This in-depth guide…
Read morePOSTED BY
Secure Debug
Mastering Passwordless Technologies: An In-Depth Guide to Modern Authentication
As organizations and users become increasingly aware of the risks, complexities, and frustrations associated with traditional password-based authentication, the adoption of passwordless technologies is gaining momentum. Passwordless solutions promise stronger security, improved user experience, and simpler management by eliminating or minimizing the reliance on static passwords. This comprehensive guide delves deep into the world of…
Read morePOSTED BY
Secure Debug
Mastering Secure Deployment and Configurations: An In-Depth Guide to Best Practices and Strategies
In today’s digital landscape, ensuring the security of applications and systems during deployment is paramount. Misconfigurations and insecure deployment practices are among the leading causes of security breaches. This comprehensive guide delves into the critical aspects of secure deployment and configurations, providing detailed insights, best practices, and strategies to safeguard your infrastructure. Whether you’re a…
Read morePOSTED BY
Secure Debug
Mastering Red Teaming: An Exhaustive Guide to Adversarial Simulation in Cybersecurity
As a cybersecurity expert with extensive experience in offensive security, I’ve witnessed firsthand the pivotal role that Red Teaming plays in fortifying an organization’s defenses. This comprehensive guide delves deep into the world of Red Teaming, providing detailed insights into methodologies, frameworks, tools, and best practices. Whether you’re a seasoned professional or new to the…
Read morePOSTED BY
Secure Debug
Top SOC Tools: An Exhaustive Guide to the Most Popular Security Operations Center Solutions
As a cybersecurity expert with years of hands-on experience in Security Operations Centers (SOCs), I’ve witnessed the critical role that specialized tools play in defending against ever-evolving cyber threats. The right combination of tools not only enhances the efficiency of a SOC but also significantly improves an organization’s overall security posture. This comprehensive guide delves…
Read morePOSTED BY
Secure Debug
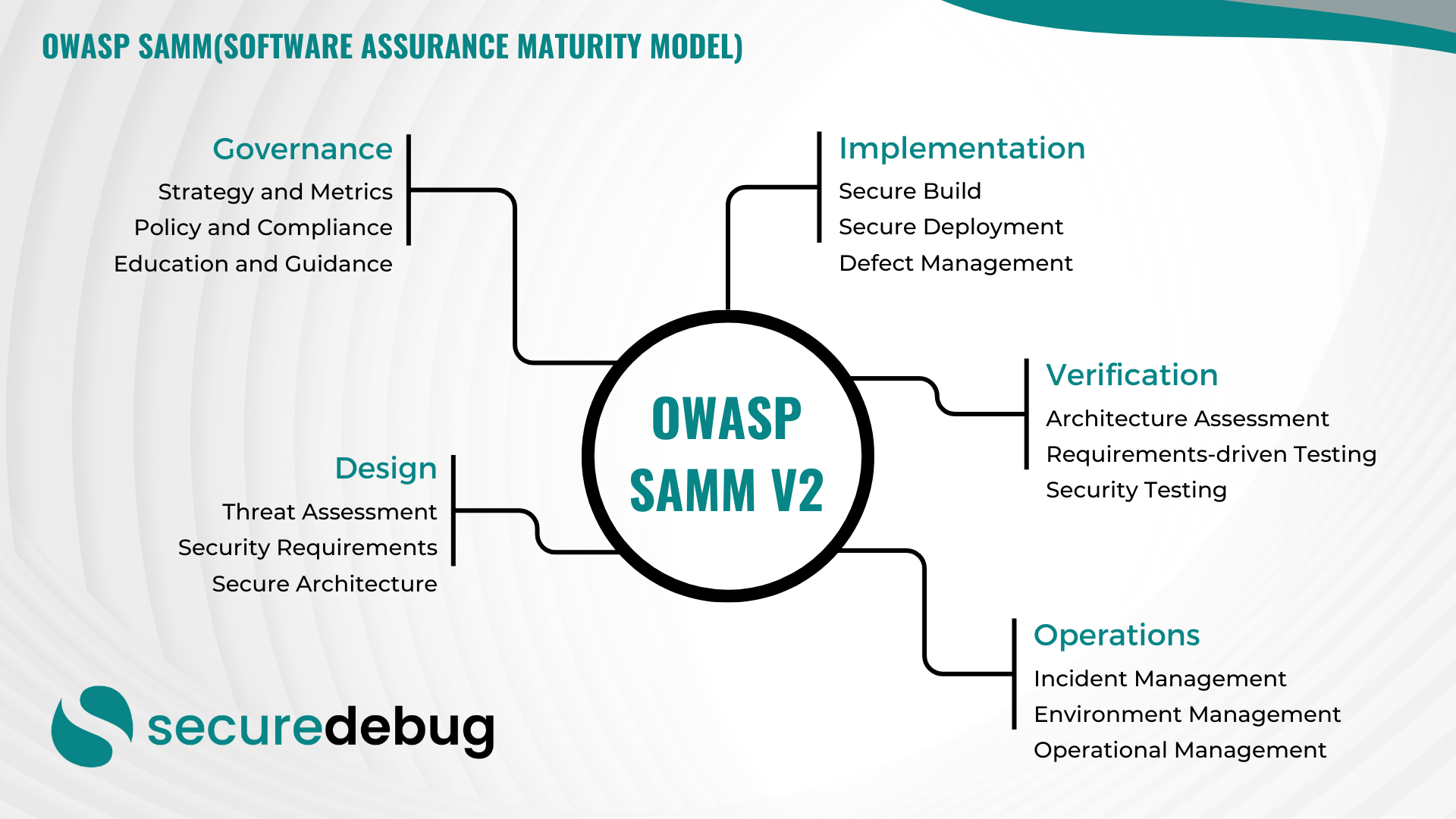
Comprehensive Guide to Implementing OWASP SAMM v2
Comprehensive Overview of OWASP Software Assurance Maturity Model (SAMM) Version 2 Introduction to OWASP SAMM v2 The OWASP Software Assurance Maturity Model (SAMM) Version 2 is an evolutionary framework designed to assist organizations in developing, enhancing, and maintaining a robust software security posture. As part of the Open Web Application Security Project (OWASP), SAMM provides…
Read morePOSTED BY
Secure Debug
Enhancing Cybersecurity in the Energy Sector: Key Strategies for Secure Debug
The Importance of Cybersecurity in the Energy Sector As the energy sector continues to digitize and rely on interconnected systems, the need for robust cybersecurity measures has never been greater. With critical infrastructure at risk of cyber attacks, it is imperative for energy companies to prioritize cybersecurity to protect against potential threats. Challenges Faced by…
Read morePOSTED BY
Okan YILDIZ
Enhancing IoT Security: A Comprehensive Guide for Secure Debug Clients
Securing Your IoT Devices: The Ultimate Guide Internet of Things (IoT) devices have revolutionized the way we live and work, but they also come with significant security risks. As a leading cybersecurity firm, Secure Debug is committed to helping our clients navigate the complex landscape of IoT sec. In this comprehensive guide, we will explore…
Read morePOSTED BY