Mastering MongoDB Security: An Ultra-Extensive Guide to Secure Configuration and Usage
MongoDB’s document-oriented nature and ease of scaling have made it a mainstay in modern development stacks—powering e-commerce, analytics, gaming, IoT, social media, and more. While its schema flexibility and high performance are compelling, these same attributes can, if not managed properly, lead to serious security oversights. Cybercriminals have routinely exploited misconfigured MongoDB databases, sometimes wiping…
Read morePOSTED BY
Secure Debug
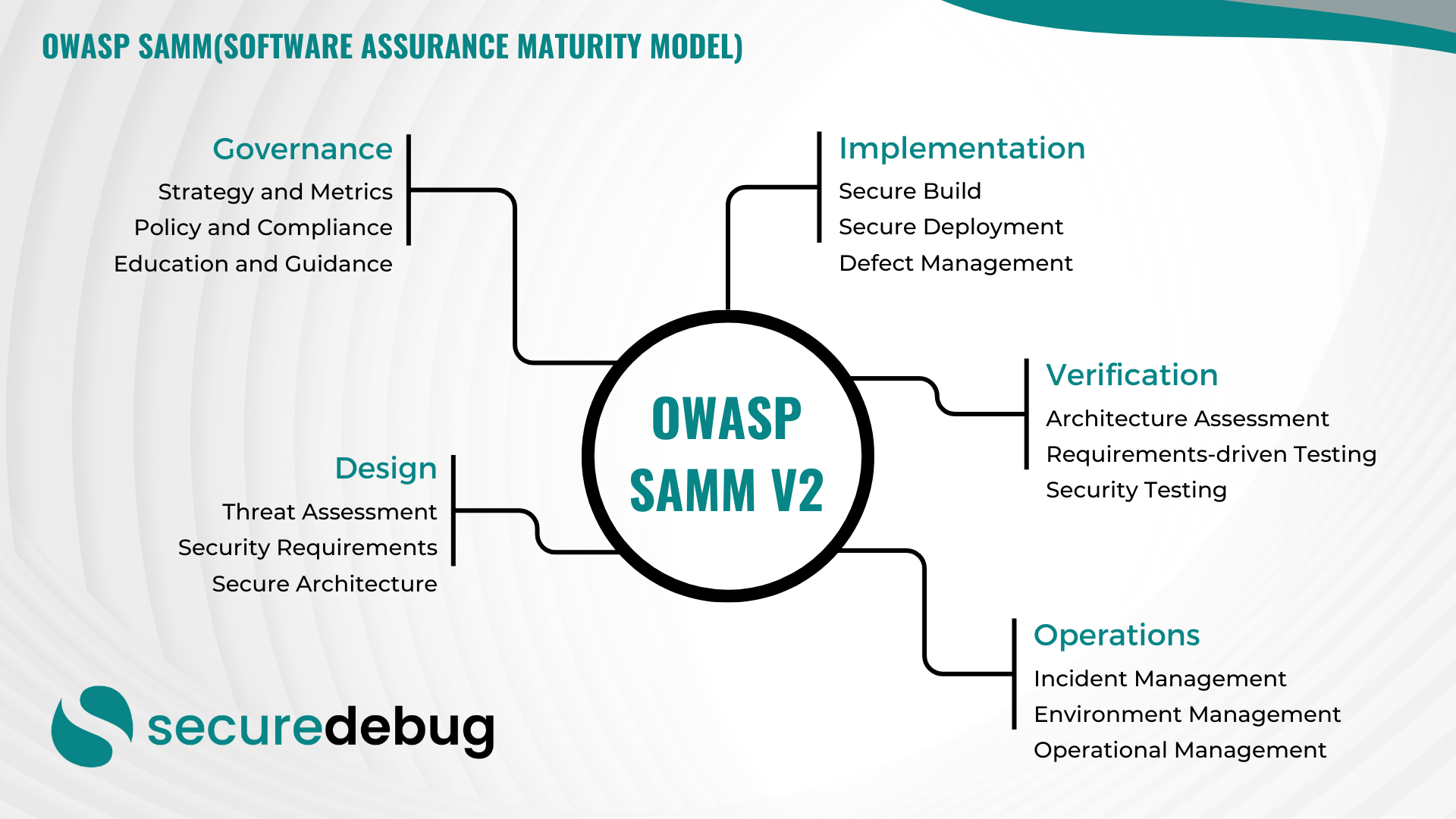
Comprehensive Guide to Implementing OWASP SAMM v2
Comprehensive Overview of OWASP Software Assurance Maturity Model (SAMM) Version 2 Introduction to OWASP SAMM v2 The OWASP Software Assurance Maturity Model (SAMM) Version 2 is an evolutionary framework designed to assist organizations in developing, enhancing, and maintaining a robust software security posture. As part of the Open Web Application Security Project (OWASP), SAMM provides…
Read morePOSTED BY
Secure Debug
Secure Code Review Practices
Secure Code Review Practices As cyber threats continue to evolve, it is crucial for organizations to prioritize secure code development practices. One such practice is secure code review, which involves a systematic analysis of the source code to identify and mitigate potential vulnerabilities. Here are some best practices to consider when conducting a secure code…
Read morePOSTED BY