Comprehensive Guide to Implementing OWASP SAMM v2
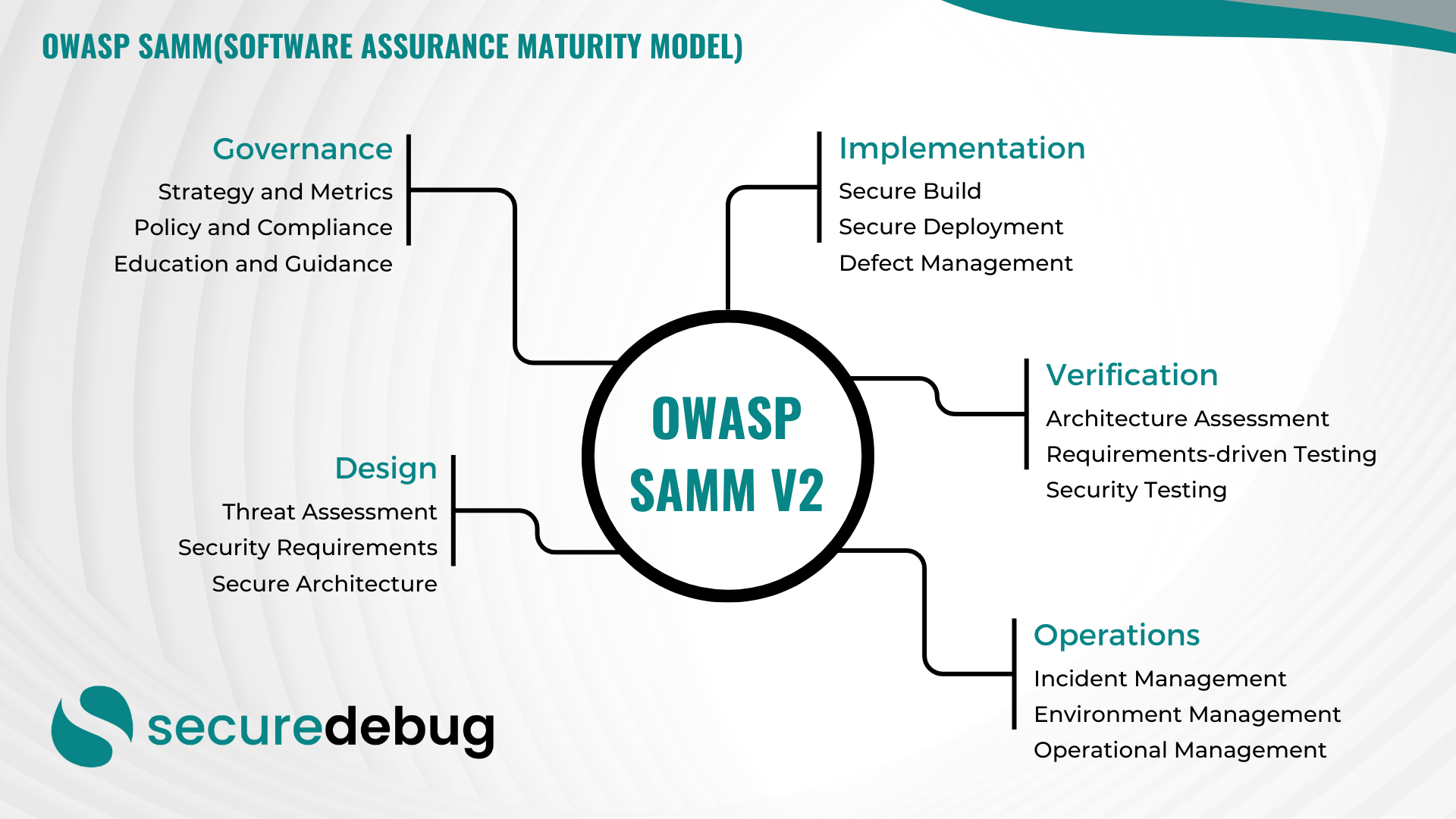
Comprehensive Overview of OWASP Software Assurance Maturity Model (SAMM) Version 2 Introduction to OWASP SAMM v2 The OWASP Software Assurance Maturity Model (SAMM) Version 2 is an evolutionary framework designed to assist organizations in developing, enhancing, and maintaining a robust software security posture. As part of the Open Web Application Security Project (OWASP), SAMM provides…
Read morePOSTED BY
Secure Debug
The Role of Application Whitelisting in Endpoint Security
The Role of Application Whitelisting in Endpoint Security Endpoint security is a critical component of any cybersecurity strategy. With the increasing number of cyber threats targeting endpoints, organizations need robust solutions to protect their networks and sensitive data. One such solution is application whitelisting, which plays a vital role in enhancing endpoint security. What is…
Read morePOSTED BY
Okan YILDIZ
Understanding Cybersecurity Reports
Introduction Welcome to Secure Debug’s cybersecurity blog! In today’s post, we will delve into the world of cybersecurity reports and their significance in protecting your organization from potential threats. Whether you are a cybersecurity professional or a business owner, understanding and leveraging these reports can greatly enhance your security posture. What are Cybersecurity Reports? Cybersecurity…
Read morePOSTED BY