Comprehensive Guide to Implementing OWASP SAMM v2
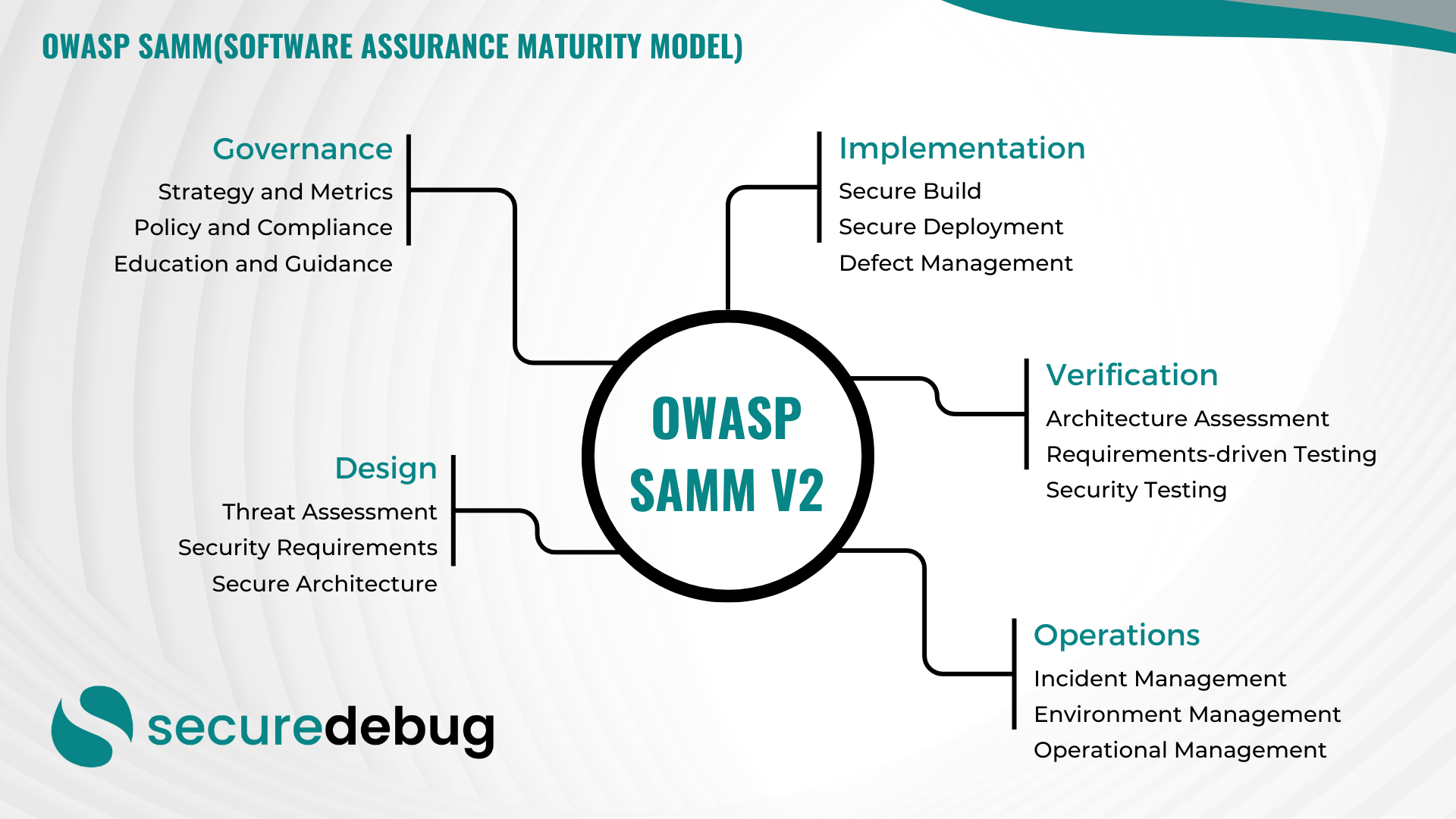
Comprehensive Overview of OWASP Software Assurance Maturity Model (SAMM) Version 2 Introduction to OWASP SAMM v2 The OWASP Software Assurance Maturity Model (SAMM) Version 2 is an evolutionary framework designed to assist organizations in developing, enhancing, and maintaining a robust software security posture. As part of the Open Web Application Security Project (OWASP), SAMM provides…
Read morePOSTED BY
Secure Debug
Implementing Secure Development Lifecycle (SDL) for Robust Cybersecurity
Introduction to Secure Development Lifecycle (SDLC) Secure Development Lifecycle (SDL) is a critical approach that integrates security practices into every phase of the software development process. By implementing SDL, organizations can identify and address security vulnerabilities early on, reducing the risk of cyber attacks and data breaches. Benefits of SDLC Implementation Implementing SDL offers numerous…
Read morePOSTED BY
Okan YILDIZ
Understanding Cybersecurity Standards: A Comprehensive Guide
Understanding Cybersecurity Standards: A Comprehensive Guide Welcome to the Secure Debug blog! In this article, we will delve into the world of cybersecurity standards and their importance in safeguarding your digital assets. As cyber threats continue to evolve and become more sophisticated, adhering to industry-standard security practices is crucial for businesses and individuals alike. What…
Read morePOSTED BY