Mastering Secure SDLC: An In-Depth Guide to Integrating Security into the Secure Software Development Life Cycle
In the ever-evolving landscape of cybersecurity, integrating security into the Secure Software Development Life Cycle (SDLC) is no longer optional—it’s imperative. As cyber threats become more sophisticated, ensuring that security measures are embedded at every phase of software development is crucial. This comprehensive guide delves deep into Secure SDLC practices, providing insights, methodologies, tools, and…
Read morePOSTED BY
Secure Debug
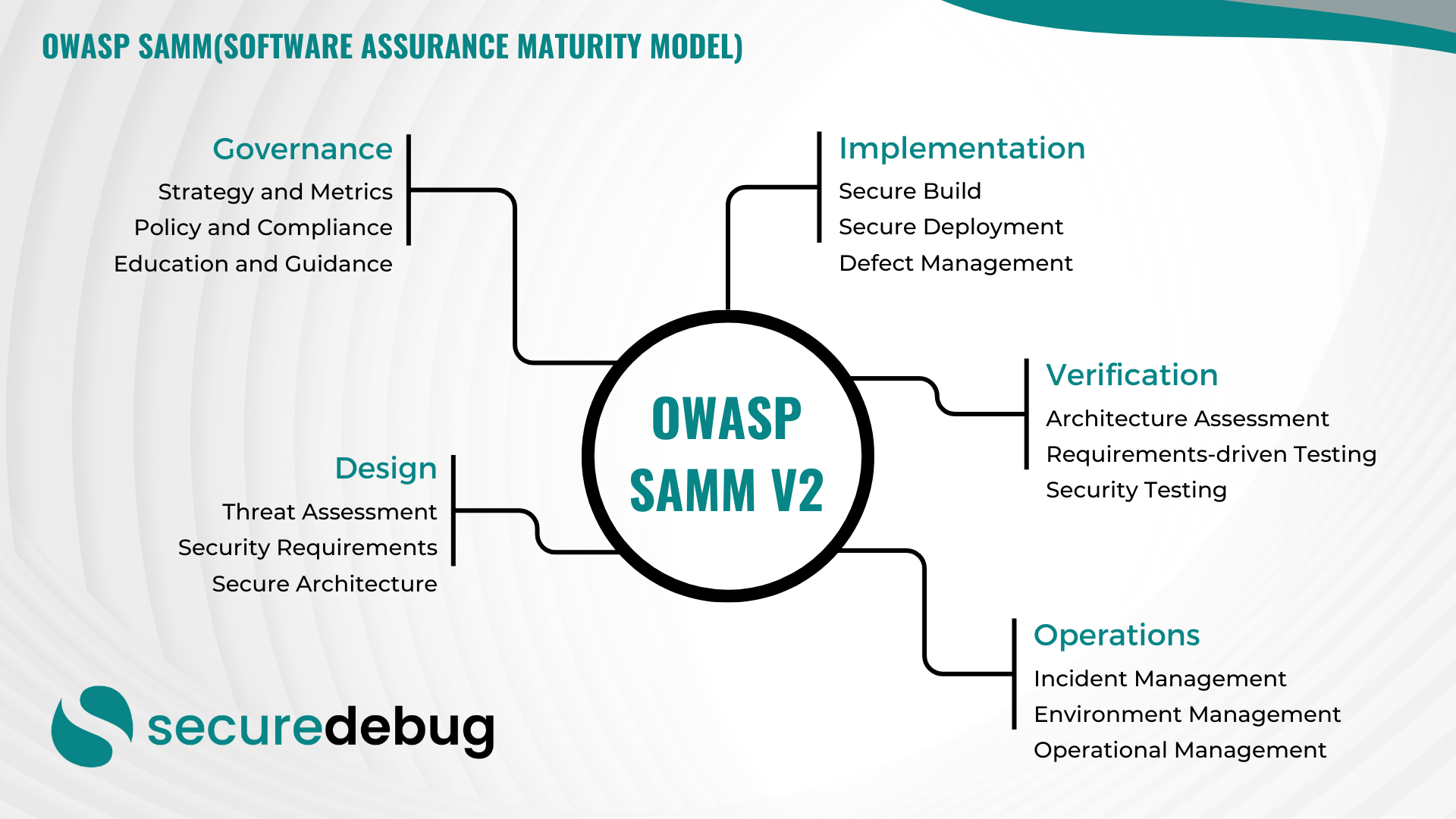
Comprehensive Guide to Implementing OWASP SAMM v2
Comprehensive Overview of OWASP Software Assurance Maturity Model (SAMM) Version 2 Introduction to OWASP SAMM v2 The OWASP Software Assurance Maturity Model (SAMM) Version 2 is an evolutionary framework designed to assist organizations in developing, enhancing, and maintaining a robust software security posture. As part of the Open Web Application Security Project (OWASP), SAMM provides…
Read morePOSTED BY
Secure Debug
Effective Remote Code Execution (RCE) Defense Strategies
Introduction Remote Code Execution (RCE) is a critical vulnerability that can allow attackers to gain unauthorized access to a system, execute arbitrary code, and potentially take complete control. To defend against RCE attacks, organizations must adopt robust defense strategies that mitigate these risks effectively. Understanding Remote Code Execution Before delving into defense strategies, it is…
Read morePOSTED BY