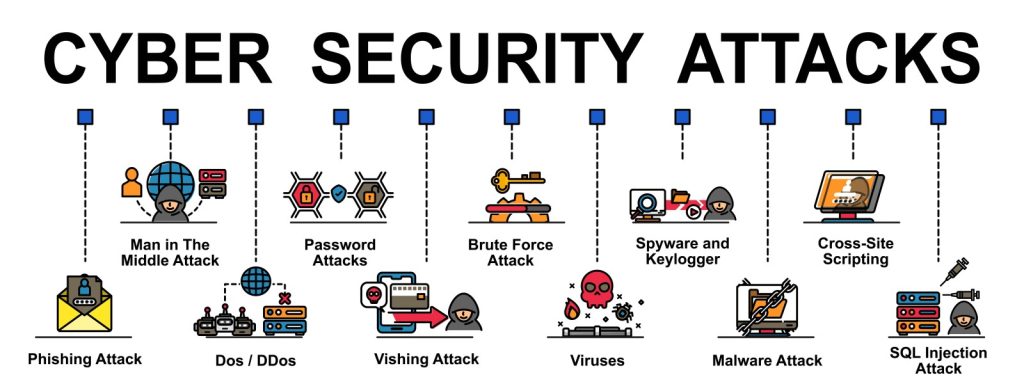
Cyber attackers use various techniques to infiltrate networks, steal sensitive data, and cause damage to systems. In this article, we will explore some of the most common methods used by cyber attackers and how you can protect your organization from them.
1) Phishing
Phishing is a social engineering technique that involves sending fraudulent emails or messages to individuals or organizations, with the goal of tricking them into revealing sensitive information, such as usernames and passwords. Phishing attacks are often used to gain access to networks or steal sensitive data, and they are one of the most prevalent forms of cyber attacks.
2)Malware
Malware is a type of software that is designed to cause harm to a computer system. Cyber attackers use various types of malware, such as viruses, worms, and Trojan horses, to infect computers and steal data or cause damage to systems. Malware can be delivered through email attachments, infected websites, or through social engineering techniques.
3)Denial of Service (DoS) Attacks
Denial of Service (DoS) attacks are designed to overwhelm a system or network with traffic, causing it to become unavailable to users. DoS attacks are often carried out using botnets, which are networks of infected computers that can be controlled remotely by cyber attackers. These attacks can cause significant disruption to businesses and organizations, particularly those that rely on their online presence for revenue or customer engagement.
4)Password Attacks
Password attacks involve using software tools to guess or crack passwords in order to gain access to networks or systems. Cyber attackers use various methods to carry out password attacks, such as brute force attacks, dictionary attacks, and social engineering techniques. Password attacks are particularly effective when users have weak or easily guessable passwords.
5)Man-in-the-Middle (MitM) Attacks
Man-in-the-Middle (MitM) attacks involve intercepting communications between two parties, such as a user and a website or application. Cyber attackers can use MitM attacks to steal sensitive information, such as usernames and passwords, or to inject malicious code into communications. MitM attacks can be carried out using various methods, such as WiFi eavesdropping or by infecting a user’s device with malware.
Protecting Your Organization
To protect your organization from cyber attacks, it is important to implement a comprehensive security strategy that includes:
- Educating employees on the dangers of cyber attacks and how to avoid them
- Implementing strong password policies and multi-factor authentication
- Keeping software and systems up-to-date with the latest security patches
- Using anti-virus and anti-malware software to protect against malicious software
- Monitoring network traffic for suspicious activity and implementing firewalls and intrusion detection systems
- Conducting regular security audits to identify vulnerabilities and address them before they can be exploited by cyber attackers.
By implementing these measures, you can significantly reduce the risk of a cyber attack and protect your organization from the devastating consequences of a security breach.







