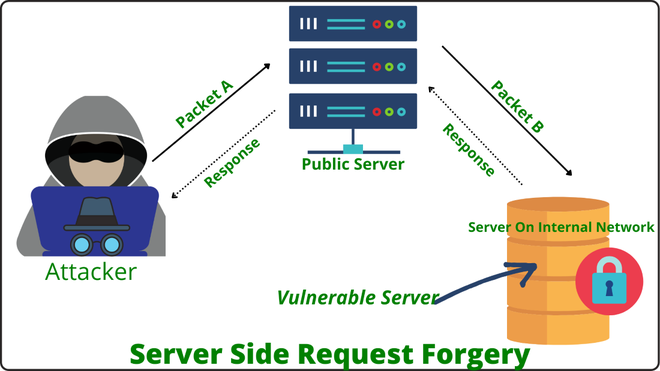
Server-Side Request Forgery (SSRF) is a critical web application vulnerability that can lead to unauthorized access, data exfiltration, and even remote code execution. This blog post delves into the details of SSRF vulnerabilities, highlighting real-world examples, effective detection techniques, and providing robust prevention strategies with code samples.
Understanding Server-Side Request Forgery (SSRF)
SSRF occurs when a web application is manipulated to issue a request on behalf of the attacker, allowing them to access internal resources or perform actions they wouldn’t normally have permission to do. SSRF typically arises when an application processes user-supplied URLs and fails to validate or restrict those URLs appropriately.
Case Study: Accessing Internal Services
Consider a web application that allows users to fetch content from external websites using a URL. If the application fails to validate the user-supplied URL properly, an attacker could exploit this by requesting internal URLs, potentially accessing sensitive information or services within the organization’s network.
Detecting SSRF Vulnerabilities
Detecting SSRF vulnerabilities often involves manual testing, using proxy tools such as Burp Suite, and manipulating input to observe the application’s behavior. Automated scanners may also be useful, but they may not identify all instances of SSRF due to the complex nature of these vulnerabilities.
Preventing SSRF Vulnerabilities
- Input Validation: Validate and sanitize user-supplied URLs to ensure they meet expected patterns and criteria. Use allowlists to permit only specific, trusted URLs or domains.
Example using Python and Flask:
from urllib.parse import urlparse
ALLOWED_DOMAINS = ['trusteddomain.com', 'anothertrusteddomain.com']
def is_allowed_url(url):
parsed_url = urlparse(url)
return parsed_url.netloc in ALLOWED_DOMAINS
@app.route('/fetch', methods=['GET', 'POST'])
def fetch():
url = request.args.get('url')
if is_allowed_url(url):
response = requests.get(url)
return response.text
else:
abort(400, 'Invalid URL')
- Restrict Network Access: Limit the network access of the application to only the necessary services and resources. This measure minimizes the attack surface in case an SSRF vulnerability is exploited.
- Monitoring and Logging: Keep track of outgoing requests and monitor for any unusual patterns or requests to internal services. Implementing monitoring and logging can help detect SSRF attacks early and aid in incident response.
- Use Safe Libraries and Functions: Use libraries and functions that are designed to prevent SSRF vulnerabilities. In some cases, this may involve replacing vulnerable functions with safer alternatives.
Conclusion
Understanding, detecting, and mitigating SSRF vulnerabilities is crucial for maintaining strong web application security. By implementing the preventative measures and incorporating code samples outlined in this blog post, you can significantly reduce the risk of unauthorized access and protect your organization’s sensitive data and internal resources.







